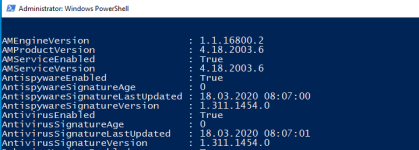
It seems like im not completely alone in this.
Like post 11 and 15 (It's about them having the same version as I,not about the problems the thread was about )
)
I hope it's not to offtopic but since WD is a mainpart of H_C I hope its ok?
Like post 11 and 15 (It's about them having the same version as I,not about the problems the thread was about
I hope it's not to offtopic but since WD is a mainpart of H_C I hope its ok?