Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
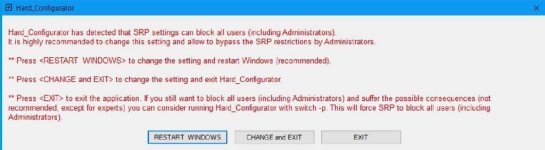
I am sorry, it seems that there is some hidden incompatibility. How did you recover the system functionality after the crash? Could you boot into Safe Mode?I updated to the new version, updated settings and firewall rules, and restarted. Similarly to when I installed the beta, the system crashed within one minute, with this error message:
View attachment 261519
I clean reinstalled 5.1.1.2, which I will probably use indefinitely, since my laptop seems to not get along with a setting in the newer versions.
Last edited: