I am finishing the new version of DocumentsAntiExploit tool.
Now it can display the Hard_Configurator settings, for example, the setting "Adobe + VBA" looks like:
View attachment 265263
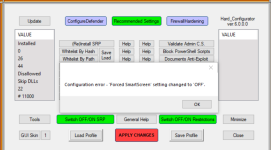
When the Hard_Configurator setting is OFF and the "Current user restrictions" are enabled, we can see:
View attachment 265264
The PV setting (Adobe Reader) means that the documents will be opened always in the "Protected View", and the ON setting is without "Protected View".
The settings for MS Office did not change. For Adobe, some new settings were added:
- bDisablePDFHandlerSwitching - disables the ability to change the specified default handler (PDF viewer).
- bDisableTrustedSites - disables and locks the ability to add privileged locations by users.
- bEnable3D - blocks 3D content.
- bEnableFlash - blocks Flash content
- iFileAttachmentPerms - prevents users from opening or launching file types other than PDF.
- iUnknownURLPerms - blocks opening URLs embedded in the PDF document.