Hard_Configurator - Windows Hardening Configurator
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
This video shows the malware already injected into the benign process. So, the infection chain is not known.
Hard_Configurator can block such malware in the earlier infection stage. The Redline stealer infection chain starts usually from the URL embedded in the email.
For example:
 resources.infosecinstitute.com
resources.infosecinstitute.com
The possibility of infection is when the user disables H_C protection or SmartScreen, because he/she is convinced that the file is benign and should be installed/executed.
Hard_Configurator can block such malware in the earlier infection stage. The Redline stealer infection chain starts usually from the URL embedded in the email.
For example:
A malicious and convincing message is sent along with an URL responsible for downloading the binary file installed on the target machine. Healthcare (taking advantage of the COVID-19 situation) and manufacturing were two industry sectors affected by this threat in the last few months.
Unmasking Redline: The Rising Malware Threat from Russia | Infosec
Dive into our full analysis of Redline, the prominent malware impacting users worldwide and trending on Russian forums.
The possibility of infection is when the user disables H_C protection or SmartScreen, because he/she is convinced that the file is benign and should be installed/executed.
F
ForgottenSeer 94654
They do not understand what a kill chain is and what disruption of the kill chain means. There should be an entire training class to teach people about this. They can handle it.This video shows the malware already injected into the benign process. So, the infection chain is not known.
Hard_Configurator can block such malware in the earlier infection stage. The Redline stealer infection chain starts usually from the URL embedded in the email.
For example:
Unmasking Redline: The Rising Malware Threat from Russia | Infosec
Dive into our full analysis of Redline, the prominent malware impacting users worldwide and trending on Russian forums.resources.infosecinstitute.com
The possibility of infection is when the user disables H_C protection or SmartScreen, because he/she is convinced that the file is benign and should be installed/executed.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
Yes, I know. But, most readers who use Hard_Configurator can understand my post.They do not understand what a kill chain is and what disruption of the kill chain means. There should be an entire training class to teach people about this. They can handle it.
- Apr 5, 2021
- 624
F
ForgottenSeer 94654
Those paths, by default Windows security, have blocked write privileges even when you are running in an admin Windows user account. Admin privileges is only granted after selecting "Continue" in the permissions notification. The behavior is similar to UAC.In the video posted, it shows the malicious executable dropped within the Microsoft.Net directory, but I was unable to paste an executable (harmless) anywhere within this path without Administrative credentials.
View attachment 266019
dronefox1166
Level 6
- Apr 18, 2022
- 277
Hi !
I have some problem, when I want to launch this extension file :
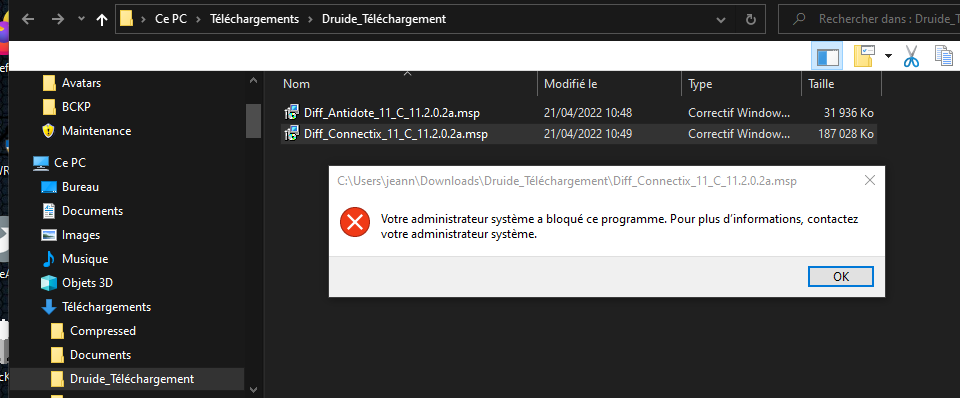
how I have to do ?
I will try to set up lonely that, but if i check I return for tell you here...
Thxx
I have some problem, when I want to launch this extension file :
how I have to do ?
I will try to set up lonely that, but if i check I return for tell you here...
Thxx
dronefox1166
Level 6
- Apr 18, 2022
- 277
I have remove *.msp files extension it's ok, but, Hard_Configurator don't want to open if I unselect this
How I have to do for open Hard_Configurator even pass by this (firt screen capture) ?
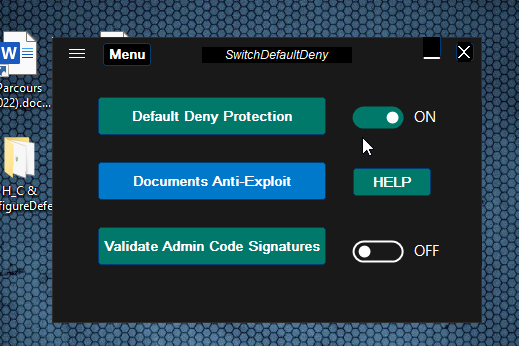
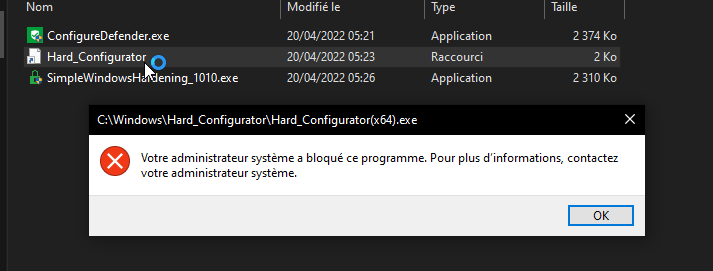
My question, why Hard_Configurator don't want to open, I am the admin ....
Since and while I have add at path whitelist C:/windows/Hard_Configurator/Hard_Configurator.exe but the problem persist... i don't know why ?
(sorry for my english I'm french, I don't know if I'm understand by you)
thx !
How I have to do for open Hard_Configurator even pass by this (firt screen capture) ?
My question, why Hard_Configurator don't want to open, I am the admin ....
Since and while I have add at path whitelist C:/windows/Hard_Configurator/Hard_Configurator.exe but the problem persist... i don't know why ?
(sorry for my english I'm french, I don't know if I'm understand by you)
thx !
Last edited:
- Apr 5, 2021
- 624
Those paths, by default Windows security, have blocked write privileges even when you are running in an admin Windows user account. Admin privileges is only granted after selecting "Continue" in the permissions notification. The behavior is similar to UAC.
Understood, but in the video demo, the malware installed to that directory without the need for the user to enter credentials.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
In the video posted, it shows the malicious executable dropped within the Microsoft.Net directory, but I was unable to paste an executable (harmless) anywhere within this path without Administrative credentials.
View attachment 266019
The file was not dropped here. The malware executed the original file from the Microsoft.Net directory and used process hollowing to run malicious code. The original file on the disk was not changed, but its image in the memory contains a malicious executable.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
What are your H_C settings? You can post here a screenshot of the H_C window. After installation, you should see the shortcuts on your Desktop. Use the Hard_Configurator shortcut from your Desktop or from Programs Menu to run H_C.I have remove *.msp files extension it's ok, but, Hard_Configurator don't want to open if I unselect this
How I have to do for open Hard_Configurator even pass by this (firt screen capture) ?
View attachment 266022
View attachment 266023
My question, why Hard_Configurator don't want to open, I am the admin ....
Since and while I have add at path whitelist C:/windows/Hard_Configurator/Hard_Configurator.exe but the problem persist... i don't know why ?
(sorry for my english I'm french, I don't know if I'm understand by you)
thx !
By the way, what is the path to the below folder? It looks like you downloaded a few files in UserSpace. Normally, execution in UserSpace is blocked, except if you use the InstallBySmartscreen option from the right-click Explorer menu. This will always execute the file (EXE, MSI) with SmartScreen check (even if it was not downloaded from the Internet).
This alert is intended to inform users that the Administrator policy is applied. You applied some policies by configuring H_C.
Last edited:
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
@sypqys
From your posts, I can recognize that you have to learn about how Windows built-in security works. Please, start from reading the H_C FAQ. It is included in the H_C manual (in the installation folder C:\Windows\Hard_Configurator). The manual and some other documents in PDF format can be accessed from the H_C window: General Help >> Documentation.It is also good to read the info included here:
Hard_Configurator – GUI to manage Software Restriction Policy (SRP) and harden Windows
dronefox1166
Level 6
- Apr 18, 2022
- 277
I have read the documentation, no entirely, but quickly, I understand more, and I have modify some things. Thxxx@sypqys
From your posts, I can recognize that you have to learn about how Windows built-in security works. Please, start from reading the H_C FAQ. It is included in the H_C manual (in the installation folder C:\Windows\Hard_Configurator). The manual and some other documents in PDF format can be accessed from the H_C window: General Help >> Documentation.
It is also good to read the info included here:
Hard_Configurator – GUI to manage Software Restriction Policy (SRP) and harden Windows
hard-configurator.com
dronefox1166
Level 6
- Apr 18, 2022
- 277
- Apr 5, 2021
- 624
The file was not dropped here. The malware executed the original file from the Microsoft.Net directory and used process hollowing to run malicious code. The original file on the disk was not changed, but its image in the memory contains a malicious executable.
That explains it. Thank you.
- Apr 5, 2021
- 624
@Andy Ful
I was still puzzled as to "how did Andy know Process Hollowing was used?" Then after clicking the blurry image in Figure 3 and doubling it's size, I could finally just see with my gradually aging and diminishing eyesight, the RunPE task the malware uses
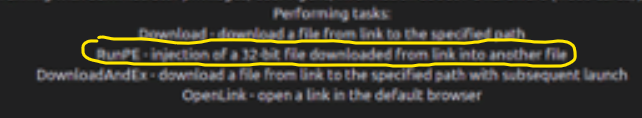
Thanks again for explaining this
I was still puzzled as to "how did Andy know Process Hollowing was used?" Then after clicking the blurry image in Figure 3 and doubling it's size, I could finally just see with my gradually aging and diminishing eyesight, the RunPE task the malware uses

Thanks again for explaining this
F
ForgottenSeer 94654
@Andy Ful
- Desired State Configuration (DSC) has been abandoned by Microsoft, it just has not released an official notice
- WDAC is rumored to be heading towards abandonment as too many clients complain about the configuration and maintenance complexity; but as with SRP, AppLocker and GPO, Microsoft might solve the problem by providing pre-configured templates following NSA\CIS recommended best practices
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
WDAC management can be simplified just like SRP. But, WDAC is less flexible.@Andy Ful
- Desired State Configuration (DSC) has been abandoned by Microsoft, it just has not released an official notice
- WDAC is rumored to be heading towards abandonment as too many clients complain about the configuration and maintenance complexity; but as with SRP, AppLocker and GPO, Microsoft might solve the problem by providing pre-configured templates following NSA\CIS recommended best practices
F
ForgottenSeer 94654
WDAC can be simplified, but I do not think that will happen. The WDAC team has made it at the same level of complexity as SE Linux. The administration and maintenance is too much for many people to handle. And since Microsoft is not talking much about WDAC lately, it follows their pattern of a project that will stall or be abandoned.WDAC management can be simplified just like SRP. But, WDAC is less flexible.
WDAC can be saved by templates provided by Microsoft or CIS.
We will just have to wait and see what happens.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
WDAC can be simplified, but I do not think that will happen.
I have in mind that its management can be simplified by some developers (like me). Microsoft did not simplify the management of SRP and Applocker, so it is probable that WDAC will share a similar fate.
Similar threads
- Replies
- 253
- Views
- 38,229
-
- Sticky
Serious Discussion
WHHLight - simplified application control for Windows Home and Pro.
- Replies
- 403
- Views
- 57,215
Serious Discussion
Why do you use obsolete security technologies such as SRP?
- Replies
- 7
- Views
- 1,667