Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,970
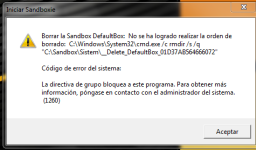
Thanks for the info and for submitting false positives.The x86 installer was detected as malware by multiple scanners. I submitted false positive reports to some of them, but according to Avast it was not a false positive.
"
Hello,
Thank you for reporting this.
Our virus specialists have confirmed that this detection is indeed correct due to lack of compliance with our clean software policy.
You can find further details in the following article: Avast Clean Guidelines.
With regards,
Avast Customer Care
"
I asked them why, but they haven't responded yet
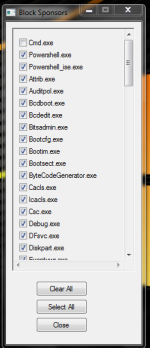
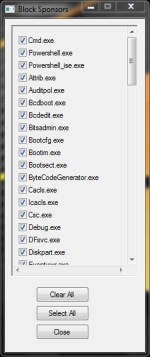
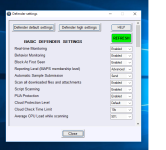
The same problem was with Windows Defender until I contacted with Microsoft for manual analysis. The problem is with popular 'Inno Setup' (www.jrsoftware.org), which I use to make Hard_Configurator installer. Inno Setup was also used recently to hide the malware in installers for Windows 32-bit, so many AVs started to flag Inno Setup installers as malicious.
I sent a reclamation to Avast. We will see how they respond.