Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
It is really weird. I assume that you close Adobe DC each time after changing the settings.
When you use <Enable All Features> after opening the document, is it added to Privileged Locations?
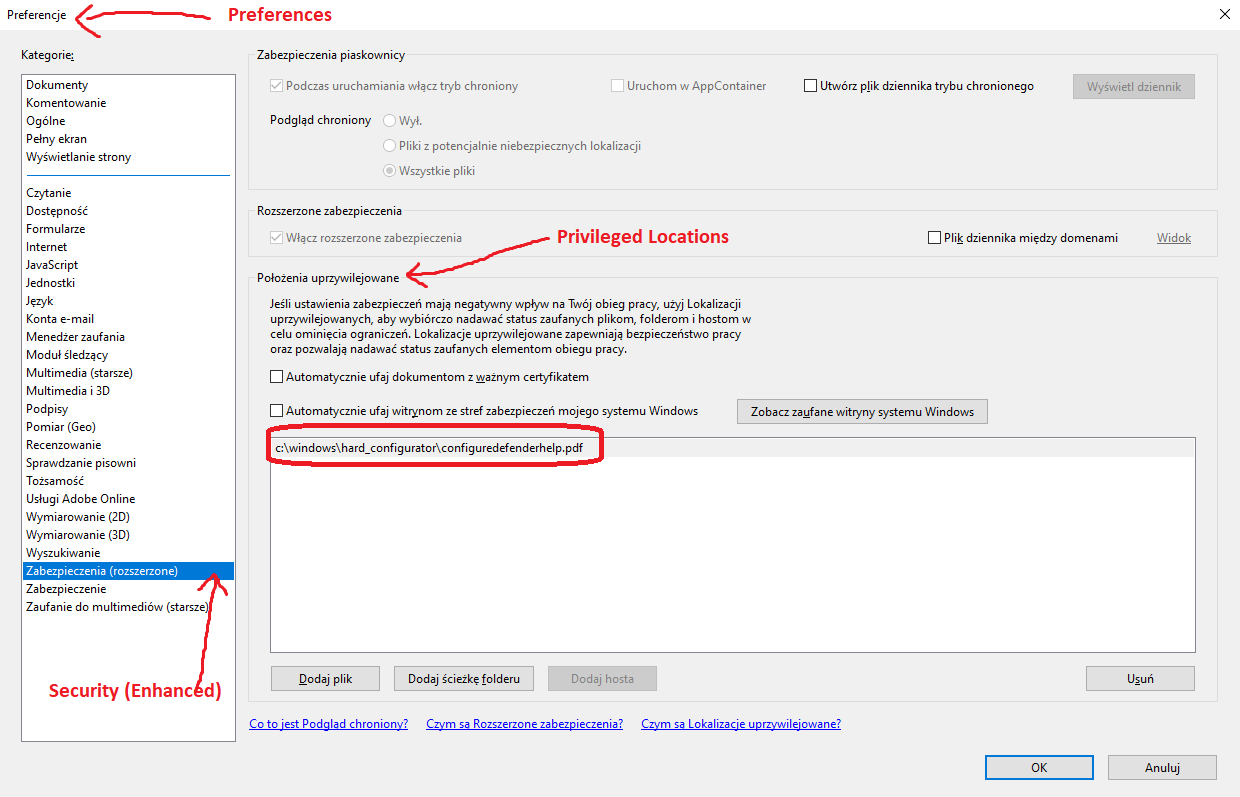
When you use <Enable All Features> after opening the document, is it added to Privileged Locations?