Restricting PowerShell on Windows 10.
PowerShell code is usually run as follows:
- By clicking (or using Enter key): on the file icon from Desktop, or on the file entry from Explorer.
- By using a command-line with PowerShell interpreter (powershell.exe or powershell_ise.exe) to run the PowerShell script files from local disk.
- By using a command-line to run PowerShell commands. This can be used to run PowerShell code (also script files) from remote locations.
- By running PowerShell interpreters in interactive mode and copy-paste the code into PowerShell console.
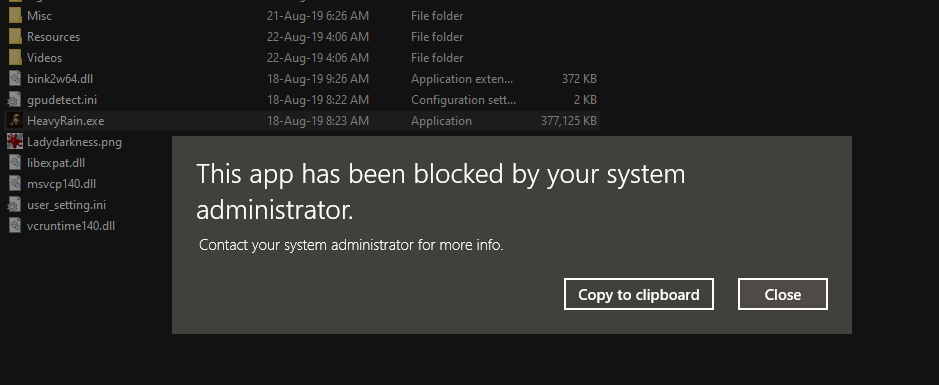
The method from point 1. is forbidden by Windows default settings on Windows 7+. This behavior is forced by H_C settings via SRP on Windows Vista.
Both methods from points 1. and 2. are blocked by the H_C option
<Block PowerShell Scripts> independently of Windows settings from point 1. The scripts are blocked when running with standard or administrative rights, so cannot be run also by system processes. This is not an issue, because system processes use PowerShell functions via System.Management.Automation.dll, which is not blocked by H_C.
The methods from points 2., 3., and 4. are restricted via the integration of PowerShell 5.0 with SRP (in default-deny setup). PowerShell 5.0 is built by default in all Windows 10 versions. This restricts PowerShell to use only features allowed by
Constrained Language mode, when PowerShell is running with standard rights. This mode disables most of the advanced PowerShell capabilities, including those commonly used in exploit kits.
When SRP is set to default-allow, or earlier PowerShell version is used, then this restriction is not available. So, in Windows Vista, 7, 8, and 8.1 the H_C settings force blocking PowerShell interpreters via SRP. This can be seen when looking into
<Block Sponsors> in H_C.
On Windows 10, PowerShell interpreters are also blocked in advanced H_C profiles, together with some other dangerous LOLBins.
When PowerShell is run by the user in interactive mode, with standard rights and H_C default-deny settings, then it uses Constrained Language mode. If PowerShell is run with administrative rights, then it is not restricted (uses Full Language mode).
Summary of H_C (default-deny) restrictions related to PowerShell.
On Windows versions prior to Windows 10, the PowerShell is blocked - with the exception of System.Management.Automation.dll .
On Windows 10, the PowerShell scripts from local sources are blocked. PowerShell can be used to run
command-lines or in the interactive mode. Yet, when running with standard rights, it is restricted by Constrained Language mode, which can block most techniques used by fileless malware.