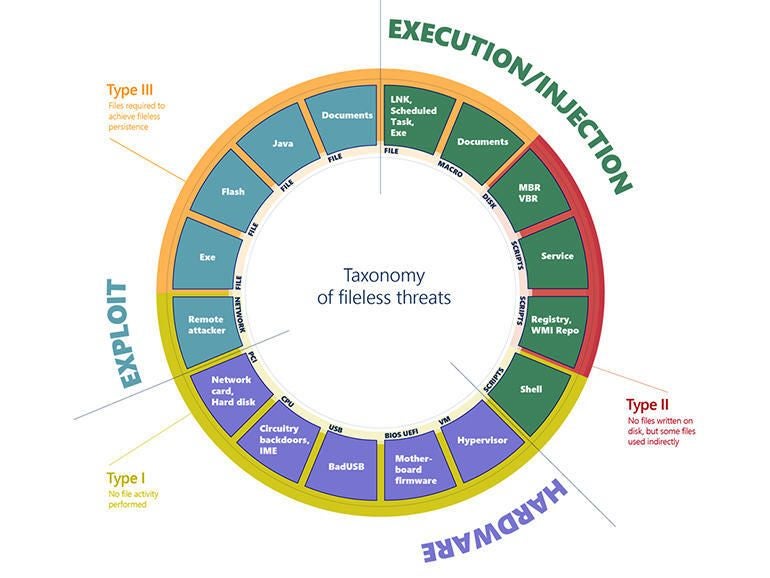
H_C and fileless malware - an example.
Here is the infection chain of the Astaroth variant attack:
The malware link on
stage 1 can be blocked by WD Network protection, but not if it is never seen malware. So the ZIP archive would be probably downloaded and the user will run the shortcut (LNK file) from this archive. But generally, shortcuts in H_C default-deny settings are blocked in UserSpace and this will stop the attack.
Let's suppose that we have another variant without intermediate LNK file. So, the user will run the BAT file instead. This also will be blocked, because BAT scripts are blocked in UserSpace.
We can imagine that another attack variant could somehow get to
stage 2 (or 3) and WMIC was run. This will be stopped either when H_C's enhanced profile is applied or <Recommended H_C> outbound block rules in FirewallHardening are applied.
WMIC command will be also blocked if ConfigureDefender MAX Protection Level is applied.
On
stage 4, the attack can be blocked when H_C's enhanced profile was applied which blocks running Bitsadmin.exe . It should be remembered that downloading by Bitsadmin.exe cannot be blocked via outbound firewall rules.
On the
later stage, H_C could break the infection chain via custom settings by blocking Regsvr32.exe or Certutil.exe.
Anyway, blocking sponsors (Wmic.exe, Bitsadmin.exe, Certutil.exe, Regsvr32.exe) is usually not necessary because in most cases the infection chain can be broken by blocking shortcuts or scripts.
Scanning files you open and save isn't enough to catch malware these days. Here's how Microsoft Defender tools can help you catch attacks that are missed by traditional security software.
www.techrepublic.com