Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,882
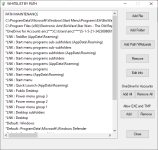
The shortcut is located too deep in the Start Menu, so it is blocked.Whitelisting the start menu folder for that fixed it for me. All good now.
So - Running H_C Recommended Settings and ConfigureDefender as High the best settings to have? I should really get around to reading the manual about FirewallHardening though I expect what I'm using now will probably suffice.
Erz
The folder C:\ProgramData\Microsoft\Windows\Start Menu (and its subfolders, too) is not writable for standard processes, so it can be whitelisted.
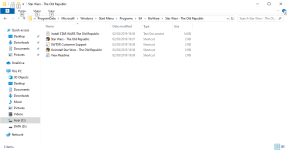
You could also make it work without whitelisting by moving the shortcut:
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\EA\BioWare\Star Wars - The Old Republic\Star Wars - The Old Republic.lnk
to:
C:\ProgramData\Microsoft\Windows\Start Menu\Programs\EA\BioWare\Star Wars - The Old Republic.lnk
FirewallHardening tool is a kind of post-exploit hardening. It is not needed on Windows 10 with standard system/software updates. Anyway, using <Recommended H_C> outbound firewall block-rules usually do not hurt, so they can be used with H_C Recommended Settings.No I mean if you use H_C at the recommended settings do you still need Firewall Hardening?
Last edited: