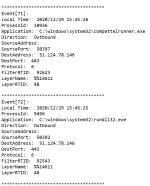
Why H_C blocks shortcuts in UserSpace?
From the article about
Microsoft Threat Protection:
Through deep correlation logic, Microsoft Threat Protection automatically finds links between related signals across domains. It connects related existing alerts and generates additional alerts where suspicious events that could otherwise be missed can be detected.
www.microsoft.com
"
Attack sprawl illustrated
The level of sophistication of today’s threats, including
nation-state level attacks and
human operated ransomware, highlight why coordinated defense is critical in ensuring that organizations are protected.
To illustrate how Microsoft Threat Protection protects against such sophisticated attacks, we asked our security research team to simulate an end-to-end attack chain across multiple domains, based on techniques we observed in actual investigations.
Their attack starts with a spear-phishing email targeting a specific user. The email contains a link that, when clicked, leads to the download of a
malicious .lnk file that stages the Meterpreter payload."
Microsoft team created a sophisticated malware, based on techniques observed in actual investigations, to show how it could be fought by Microsoft Threat Protection. Here is the full infection chain (correlated attack on 3 computers):
View attachment 244934
As can be seen, if the spear-phishing email to Polly will succeed by downloading the archive, then the infection chain on his/her computer is started by running the malicious shortcut (*.LNK file). If the shortcut will be blocked, then nothing will happen to her.
The attack on Mike's computer is improbable in the home environment, because the attacker has to know the credentials before infecting the computer (but is typical in enterprises). Anyway, it can be stopped by FirewallHardening (mshta.exe connections are disabled). Furthermore, the Windows remote features in the H_C settings are also blocked.
The attack on Marco's computer will fail because the malicious document cannot use VBA interpreter in the H_C settings (macros, etc.) to run the backdoor embedded in the MS Office document.
So, similar sophisticated attacks can be easily blocked with H_C settings in the home environment. But in enterprises, the H_C settings are not practical so the shortcuts will be allowed, the VBA interpreter will be allowed, and the remote features will be allowed. That is why something like Microsoft Threat Protection is required in enterprises and something like H_C will be useless there (but still very efficient in the home environment).