@Andy Ful
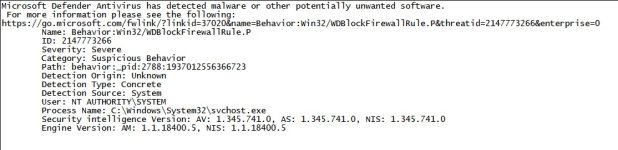
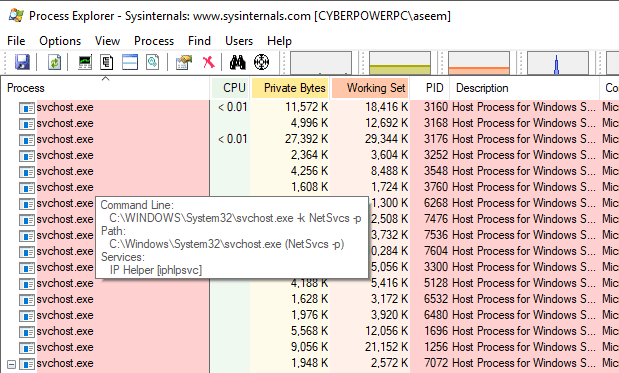
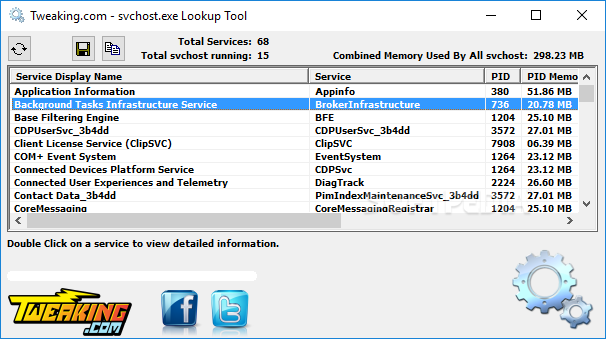
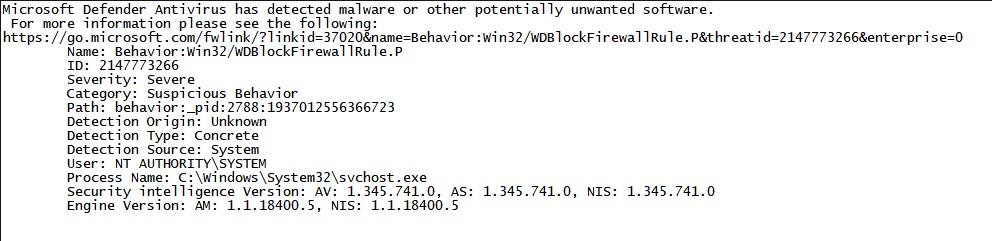
Hi Andy, is there any reason at all how Hard_Configurator could cause a Behavior:Win32/WDBlockFirewallRule.P Error?
I was just browsing the internet while it poped up...
H_C Version 5.1.1.2
H_C Recommended Settings + added block Sponsors "Script interpreters" and "Enhanced"
Configure Defender "High" with added "Block unknown files low reputation"
Firewall Hardening: Add Recommended settings.
Windows 10 Pro,19043.1165, Windows Feature Experience Pack 120.2212.3530.0
Firewall: Glasswire light in "ask to connect" mode. Current Version
It's a fresh install since I wanted to try the new 21H1.
Hi Andy, is there any reason at all how Hard_Configurator could cause a Behavior:Win32/WDBlockFirewallRule.P Error?
I was just browsing the internet while it poped up...
H_C Version 5.1.1.2
H_C Recommended Settings + added block Sponsors "Script interpreters" and "Enhanced"
Configure Defender "High" with added "Block unknown files low reputation"
Firewall Hardening: Add Recommended settings.
Windows 10 Pro,19043.1165, Windows Feature Experience Pack 120.2212.3530.0
Firewall: Glasswire light in "ask to connect" mode. Current Version
It's a fresh install since I wanted to try the new 21H1.
Attachments
Last edited: