Trojan viruses are a dangerous type of malware that gain access to computers under false pretenses in order to deliver malicious payloads. This comprehensive guide will unpack everything about how trojan viruses operate – their infection tactics, attack methods, how to spot infections, and proven steps to remove them.
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 2 Subtitles Adware removal (Subtitles.exe)](https://malwaretips.com/blogs/wp-content/uploads/2023/07/Subtitles-Adware-removal-Subtitles.exe_.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 3 Image: {KEYWORD}..exe Malware](https://malwaretips.com/blogs/wp-content/uploads/2022/12/KEYWORD..exe-malware.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 4 Honey Video & Photo Maker Trojan](https://malwaretips.com/blogs/wp-content/uploads/2023/01/Honey-Video-Photo-Maker.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 5 Image: Install.msix Trojan](https://malwaretips.com/blogs/wp-content/uploads/2023/01/install.msix-malware.jpg)
What Are Trojan Viruses?
Trojan viruses are a dangerous form of malware that infiltrate computers under false pretenses to unleash malicious and sometimes destructive attacks. Trojan viruses exhibit worm-like behavior by replicating themselves and spreading across networks and removable media.
Trojan viruses get their name from the legendary Trojan Horse tale in ancient Greek mythology. The Greeks presented a giant wooden horse statue supposedly as a gift to the people of Troy. However, it was filled with Greek soldiers hiding within the hollow sculpture. Once the horse was brought inside Troy’s defenses, the Greek soldiers emerged at night and attacked from within, winning the war.
Similarly, trojan viruses disguise themselves as useful programs or files in order to trick unwitting users into willingly downloading and installing the malware. But concealed within the appealing package is harmful software waiting to be unleashed. Once installed, trojan viruses open backdoors into infected computers for remote hackers to exploit.
Some of the most common digital disguises trojan viruses use include:
- Cracked software or game mods that promise free, unlimited access to paid programs
- Fake videos or music files like MP3s or movie trailers
- Bogus utility software like PC optimization tools or cleanup wizards
- Legitimate-looking installers bundled with trojans as added components
- Official software cunningly modified and repackaged with viral payloads
- Fake software updates that mimic real alerts from trusted programs
- Malicious email attachments pretending to be invoices or shared documents
Other trojan virus distribution tactics include compromising legitimate websites to silently push downloads to visitors, or infecting removable media like USB sticks that automatically execute malicious scripts when plugged in.
Once a trojan virus is installed on a computer, it leverages rootkit functions to bury deep within the system – modifying registries, creating hidden processes, embedding in folders, and changing configurations. This makes detection and removal much harder.
From their embedded location, trojan viruses can unleash a variety of damaging and illegal cyber attacks, including:
- Logging keystrokes and scraping screenshots or clipboard data to steal passwords, banking details, and other sensitive information
- Activating webcams and microphones to spy on victims
- Allowing backdoor remote access for hackers to fully control the computer
- Downloading additional malware such as ransomware or botnet modules
- Disabling and changing security software configurations to allow infections to persist
- Crashing systems by overloading critical resources like RAM and CPU
- Damaging files and data by overwriting, deleting, or encrypting documents
- Propagating across networks to infect more connected computers and systems
For victims, a trojan virus infection opens up their digital life to constant monitoring, identity theft, extortion, data and hardware destruction, and resources hijacked for criminal purposes.
Here are some real-world examples of dangerous trojan viruses:
- Zeus – Designed to steal banking credentials through keylogging and form grabbing. Spread via phishing and drive-by downloads.
- ZeroAccess – Turned infected computers into bitcoin-mining bots, causing extreme slowdowns.
- NanoCore – Provided hackers with remote access to clandestinely control systems and exfiltrate data.
- DarkComet – Older trojan used for cyber espionage via webcam spying, keylogging and data exfiltration.
- BlackEnergy – Infamous for enabling distributed denial-of-service (DDoS) attacks that overwhelmed targets. Also destroyed data.
- Emotet – Major banking trojan that often distributes additional spam, ransomware and banking malware modules.
These examples highlight why trojan viruses continue to rank among the most dangerous cyber threats facing computer users today. Their advanced deception tactics and malicious capabilities make them a high-risk malware threat.
How Do Trojan Viruses Infiltrate Systems?
Trojan viruses employ deceptive distribution tactics to get installed on target computers. Some of their most common infection methods include:
- Bundled downloads – The viruses get packaged within appealing but fake software installers.
- Phishing emails – Malicious attachments pretending to be documents or invoices infect systems when opened.
- clickjacking – Users get tricked into clicking disguised download buttons on compromised sites.
- Fake updates – Popups imitate software upgrade alerts to get users to download infected installers.
- Physical media – Infected USB drives or disks trigger automatic virus execution when plugged in.
- Network worms – Some trojan viruses scan for open network shares and security holes to spreadcopies of themselves.
Once installed, trojan viruses leverage rootkit functions to bury themselves in registries, folders, and processes. This makes detection and removal much harder.
Signs of a Trojan Virus Infection
Trojan viruses try to stay covert once installed. But there are some symptoms that may indicate their presence:
- Slow computer performance – Trojan viruses consume system resources which causes lag and crashes.
- Unknown processes – Check for unfamiliar processes running that don’t match your installed programs.
- Antivirus alerts – Security software may detect trojan virus behavior and block the infection.
- Disabled security settings – Trojan viruses modify configurations to disable protections.
- Network usage spikes – Unusual spikes in traffic indicate trojan viruses phoning home or spreading.
- Frequent crashes – Programs crashing or freezing constantly can point to trojan virus interference.
- Corrupted files – Trojan viruses damage files as part of data wiper or ransomware capabilities.
Any of these signals warrants a deeper scan to isolate and exterminate embedded trojan viruses.
Dangers of Trojan Viruses
Left unchecked, trojan viruses pose many threats:
- Remote system control – Hackers can fully operate the computer via backdoor access.
- Financial theft – Keyloggers and data scraping steal banking, credit card information and logins.
- Loss of sensitive data – Trojan viruses extract documents, passwords, emails and other confidential information.
- Ransomware deployment – Trojan viruses often install additional ransomware modules to extort money.
- Webcam hijacking – Criminals can spy through your webcam once a trojan virus is present.
- Zombie botnets – Your Windows system may get conscripted into hacker-controlled botnets.
- Worm propagation – Virulent trojan viruses can rapidly spread copies across networks and infect connected devices.
It is critical to quickly find and terminate trojan virus infections before additional damage can be done.
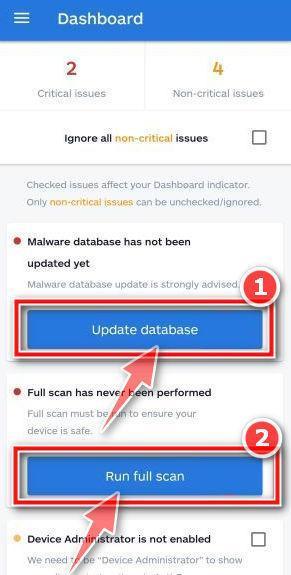
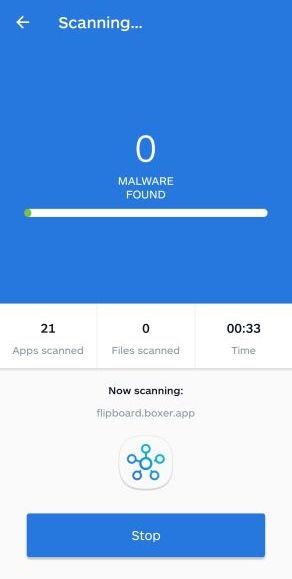
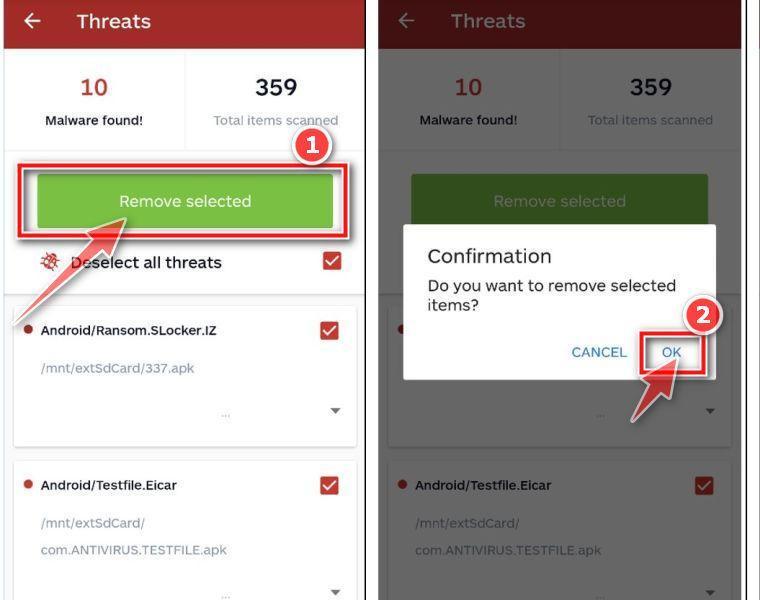
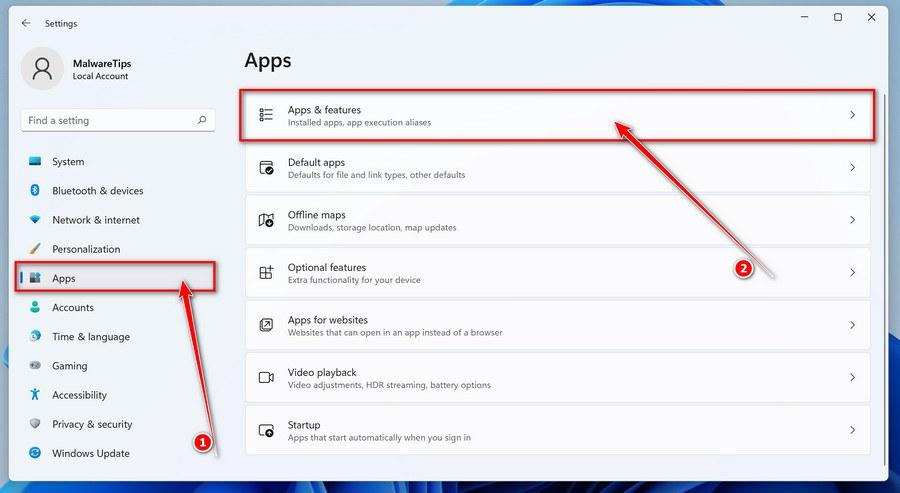
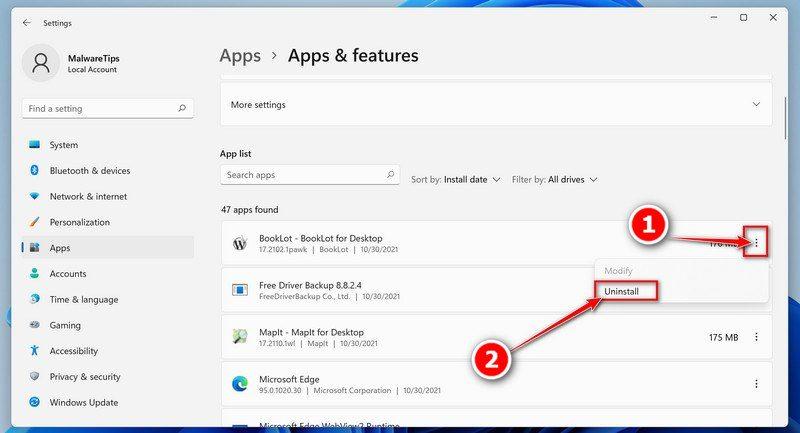
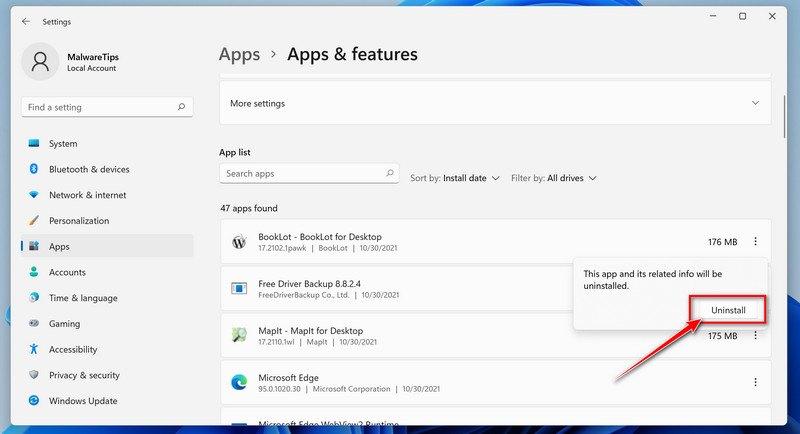
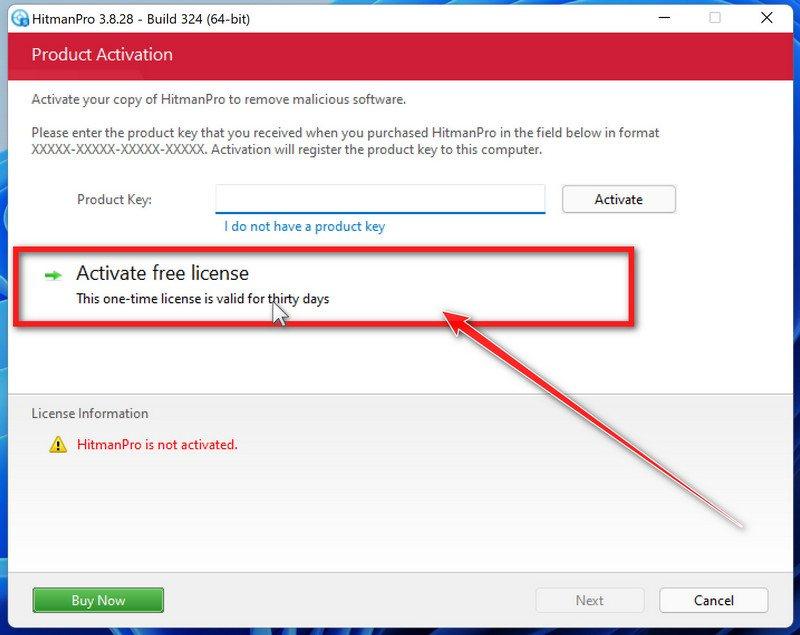
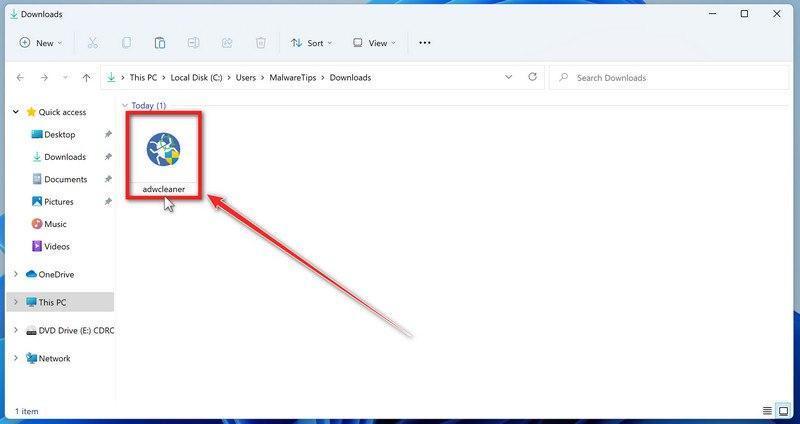
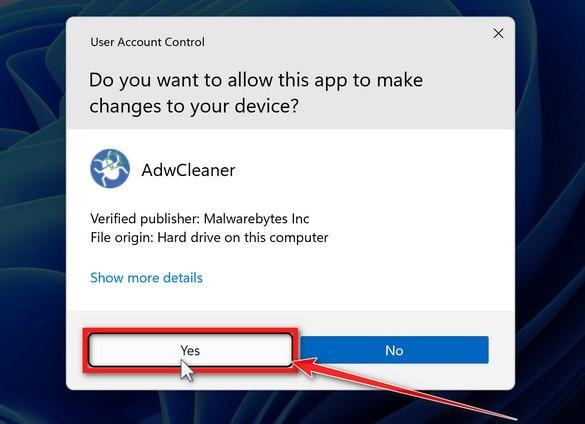
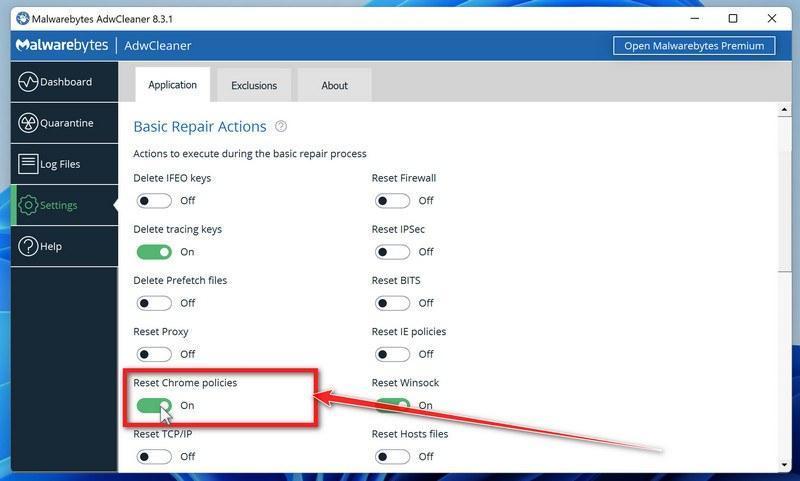
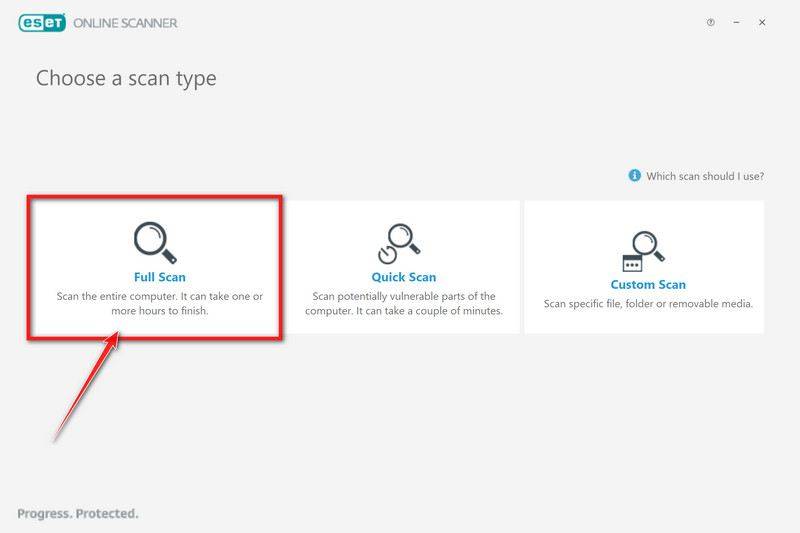
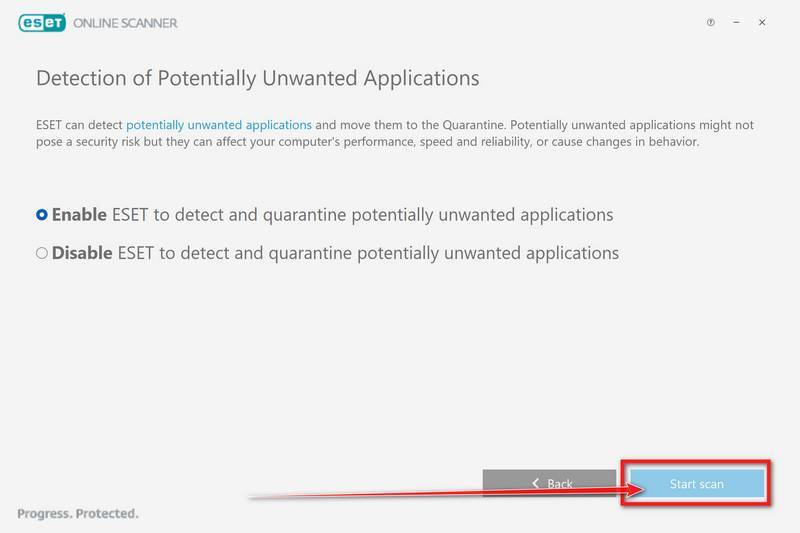
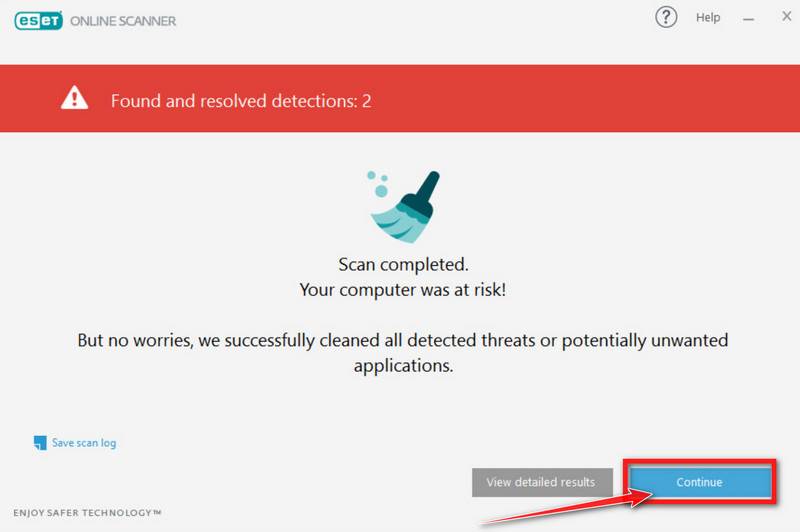
How to Check for and Remove Trojan Viruses
Please perform all the steps in the correct order. If you have any questions or doubts at any point, stop and ask for our assistance.
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 6 Windows logo](https://malwaretips.com/blogs/wp-content/uploads/2022/07/microsoft-icon-article.png) Remove Trojan Viruses from Windows
Remove Trojan Viruses from Windows-
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 7 apple icon article](https://malwaretips.com/blogs/wp-content/uploads/2022/07/apple-icon-article.png) Remove Trojan Viruses from Mac
Remove Trojan Viruses from Mac ![How to Remove a Trojan Virus from Windows [Rmoval Guide] 8 Android logo](https://malwaretips.com/blogs/wp-content/uploads/2022/07/android-icon-article.png) Remove Trojan Viruses from Android
Remove Trojan Viruses from Android
Protecting Against Future Trojan Virus Attacks
Preventing trojan viruses from ever gaining a foothold is just as critical as removing existing ones. Follow cyber hygiene best practices:
- Maintain updated antivirus, firewall, and anti-malware software. Schedule regular scans.
- Never open email attachments or click links from random or suspicious messages.
- Avoid downloading programs from unofficial sites – stick to reputable sources only.
- Install browser extensions like ScriptSafe to block untrusted code on pages.
- Make periodic backups of your operating system and files in case you need to reset your computer.
- Be wary of public USB charging stations which could deploy USB trojan virus infections.
Layers of proactive precautions will greatly minimize vulnerabilities that trojan viruses exploit to infiltrate systems and proliferate.
Frequently Asked Questions on Trojan Viruses
Trojan viruses employ devious tricks to infect computers undetected. This FAQ answers common questions on how trojan viruses work, how to remove them, and how to stay protected.
What are the most common ways trojan viruses spread?
Fake downloads, malicious email attachments, compromised sites, infected USB drives, and worm propagation via networks are some of the most common infection methods.
What are signs my device has a trojan virus?
Unfamiliar processes running, antivirus alerts, disabled security settings, system slowdowns, frequent crashes, network spikes, and corrupted files are potential indicators.
What sensitive data are trojan viruses trying to steal?
Keyloggers and clipboard scraping aim to steal passwords, bank/credit card details, social security numbers, private documents, emails, and any other valuable info.
Can a trojan virus take over my webcam and spy on me?
Yes, trojan viruses can covertly activate webcams and microphones to spy on victims without their knowledge once installed.
How do trojan viruses hide themselves so well from antivirus?
They use rootkit techniques to conceal themselves in system folders, registries, and processes under stealthy names. This makes detection harder.
How do I fully remove a trojan virus infection?
Layer antivirus scans, anti-malware cleaning, monitor traffic, reinstall affected programs, reset system configurations, and reformat from a clean OS backup if needed.
Is completely removing an advanced trojan virus infection difficult?
Yes, the most sophisticated strains require persistence and a combination of tools to fully erase due to their embedding capabilities.
Can my iPhone or Android get infected by a trojan virus?
Yes, trojan viruses can infect iOS and Android devices, though Apple and Google app vetting make this less common than on Windows. Still risky though.
Should I avoid opening email attachments to protect against trojan viruses?
Definitely – opening attachments from any suspicious or unknown sender is extremely high-risk and a common trojan virus infection tactic.
What’s the best way to prevent trojan virus infections in the future?
Always install software only from official sources, don’t click random links or pop-ups, scan downloads with antivirus, avoid piracy sites, and maintain security tools.
By understanding their distribution methods and removal techniques, users can avoid falling victim to dangerous trojan virus infections. Prevention is always the best defense against malware.
The Bottom Line
Trojan viruses employ deceptive tricks straight from ancient mythology to disguise themselves as legitimate software and bypass security controls – only to unleash malicious actions from within compromised computers.
Spotting the subtle indicators of trojan virus infections and leveraging antivirus, anti-malware, monitoring, reinstalling programs, and system backups allows you to seek out and destroy even advanced trojan virus strains.
Vigilant cyber hygiene practices provide critical prevention to keep these insidious threats locked out of your devices and networks. With proper precautions and removal methods in place, trojan viruses need not be your Achilles’ heel.

![How to Remove a Trojan Virus from Windows [Rmoval Guide] 9 RKILL Window](https://malwaretips.com/blogs/wp-content/uploads/2023/01/RKILL-2.jpg)
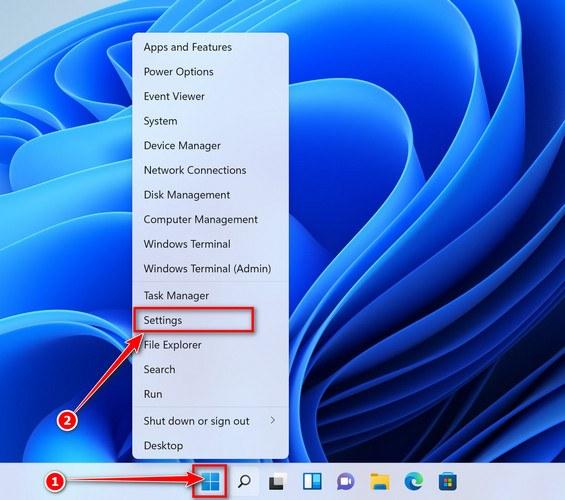
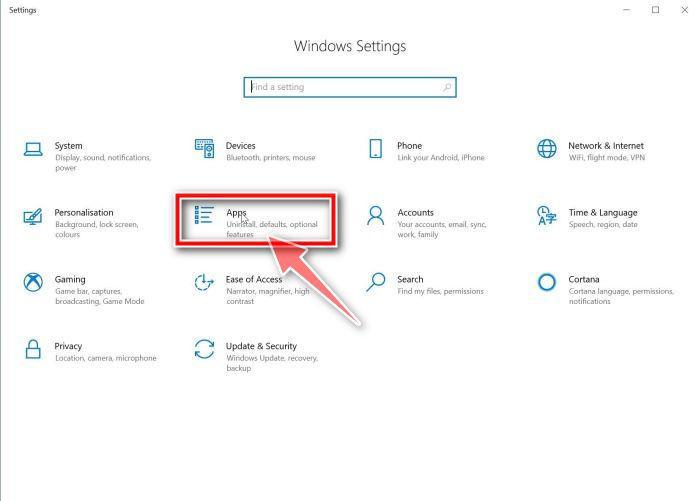
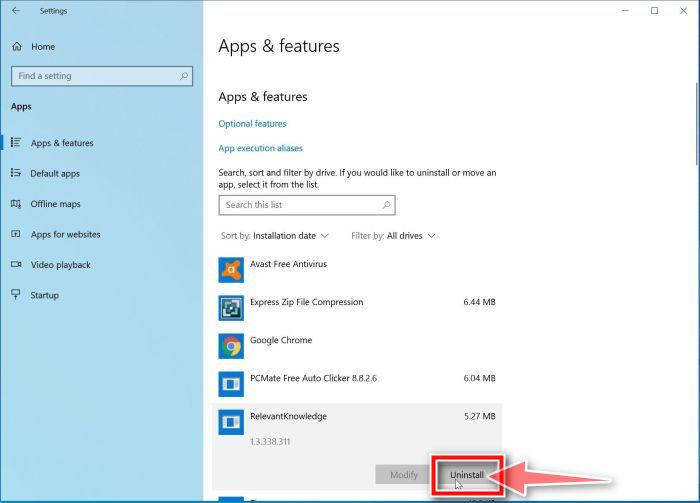
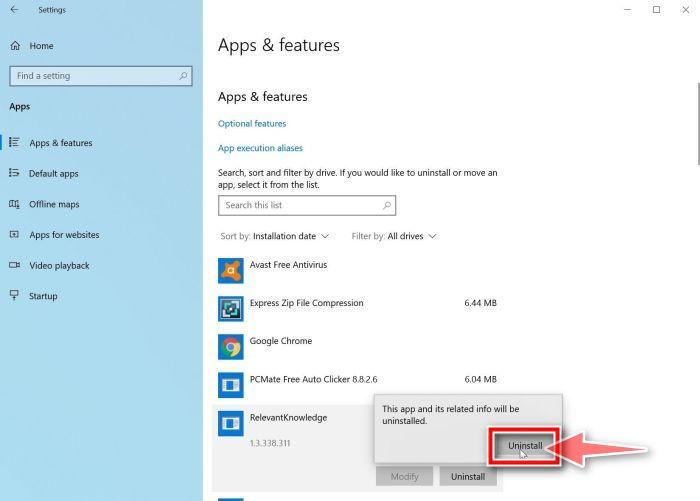
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 10 Right click on Start and select Programs and Features](https://malwaretips.com/blogs/wp-content/uploads/2020/04/Windows-8-1-Programs-and-Features.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 11 Select malicious program then click on Uninstall](https://malwaretips.com/blogs/wp-content/uploads/2020/04/Uninstall-Programs-in-Windows-8.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 12 Windows 7 go to Control Panel](https://malwaretips.com/blogs/wp-content/uploads/2020/04/windows-7-start-menu-control-panel.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 13 Select Uninstall malicious program from Control Panel](https://malwaretips.com/blogs/wp-content/uploads/2020/04/uninstall-a-program-windows-7.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 14 Uninstall malware from Windows 7](https://malwaretips.com/blogs/wp-content/uploads/2020/04/uninstall-Windows-7-Programs.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 15 Chrome 1a](https://malwaretips.com/blogs/wp-content/uploads/2025/06/Chrome-1a.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 16 Chrome 1b](https://malwaretips.com/blogs/wp-content/uploads/2025/06/Chrome-1b.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 17 Chrome 2](https://malwaretips.com/blogs/wp-content/uploads/2025/06/Chrome-2.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 18 Chrome 3 1](https://malwaretips.com/blogs/wp-content/uploads/2025/06/Chrome-3-1.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 19 Chrome 4](https://malwaretips.com/blogs/wp-content/uploads/2025/06/Chrome-4.jpg)
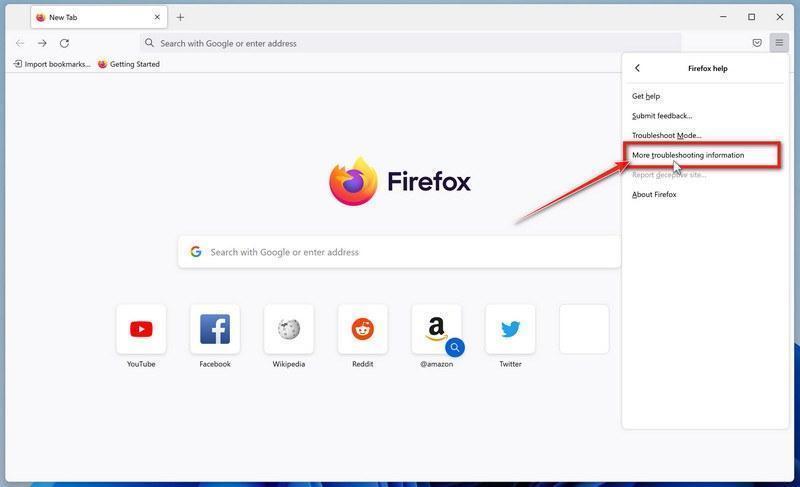
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 20 Click on Refresh Firefox](https://malwaretips.com/blogs/wp-content/uploads/2022/04/Refresh-Firefox-button.jpg)
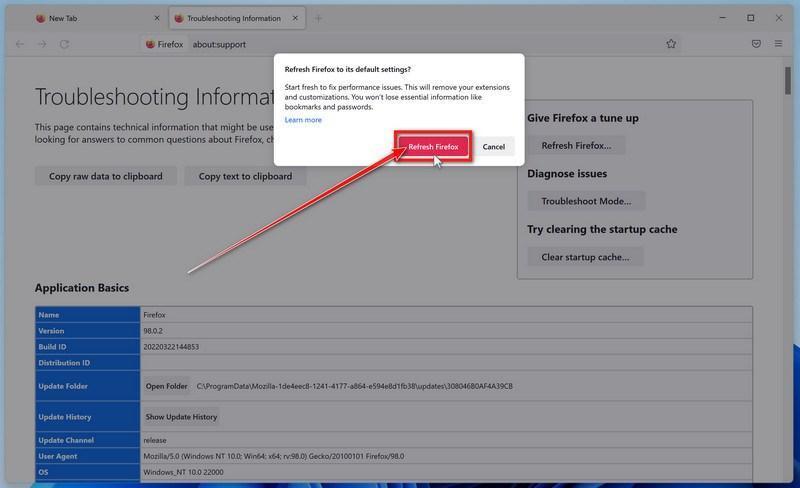
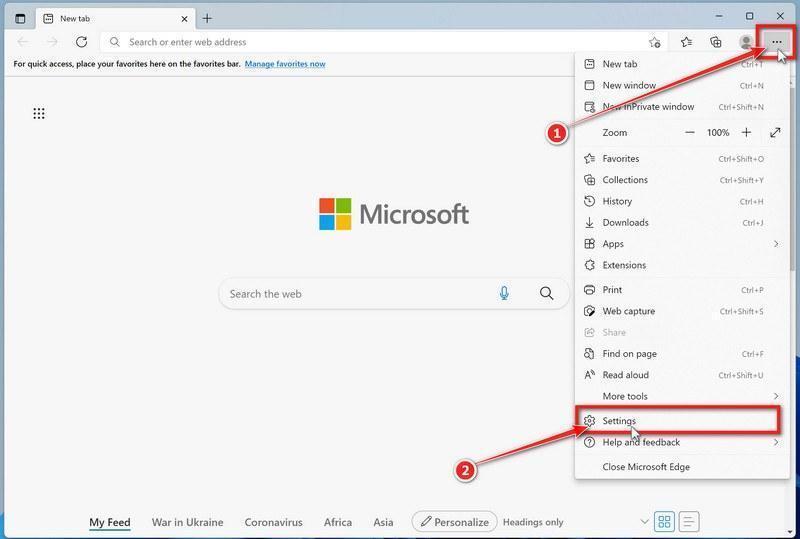
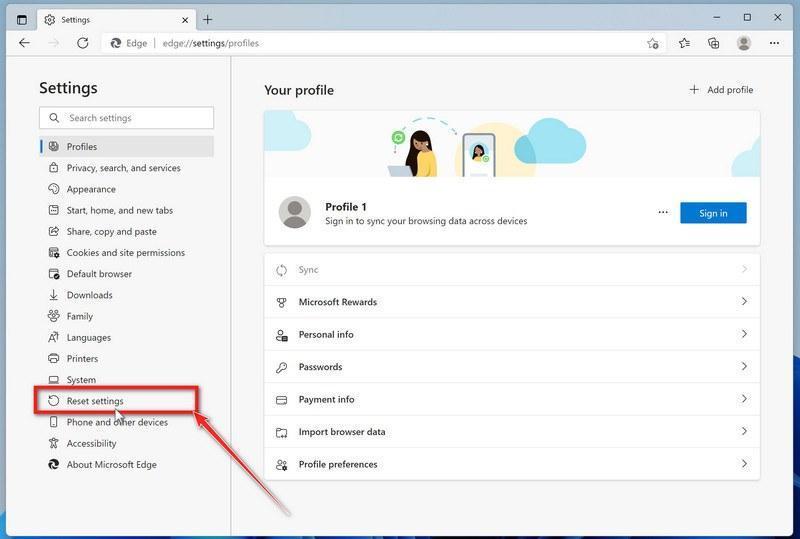
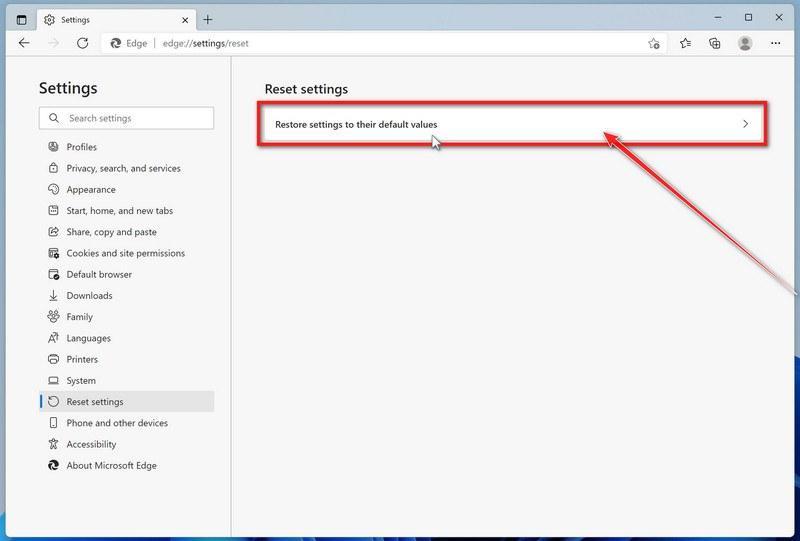
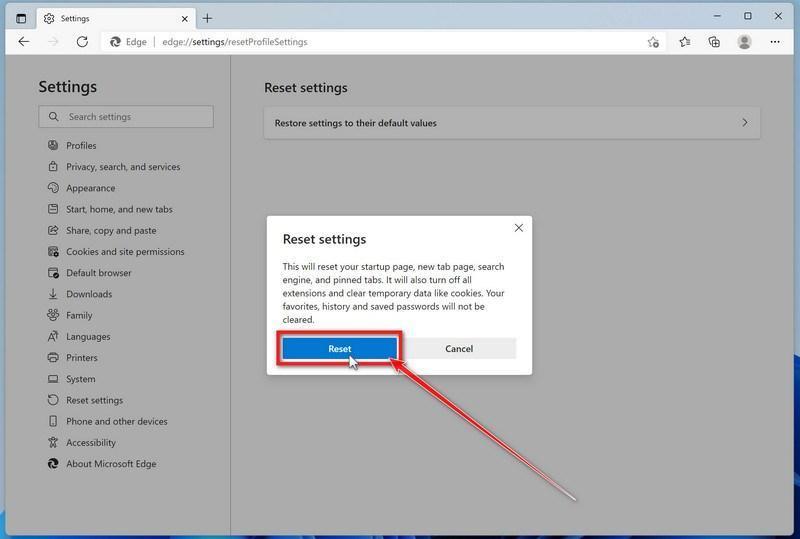

![How to Remove a Trojan Virus from Windows [Rmoval Guide] 21 MBAM1](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM1.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 22 MBAM3 1](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM3-1.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 23 MBAM4](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM4.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 24 MBAM6 1](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM6-1.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 25 MBAM5 1](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM5-1.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 26 MBAM8](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM8.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 27 MBAM9](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM9.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 28 MBAM10](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM10.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 29 MBAM11](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM11.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 30 MBAM12](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM12.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 31 MBAM13](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM13.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 32 MBAM14](https://malwaretips.com/blogs/wp-content/uploads/2024/05/MBAM14.jpg)
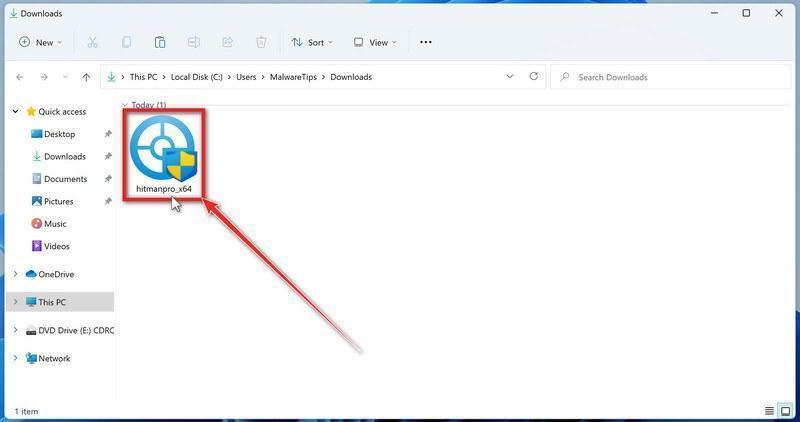
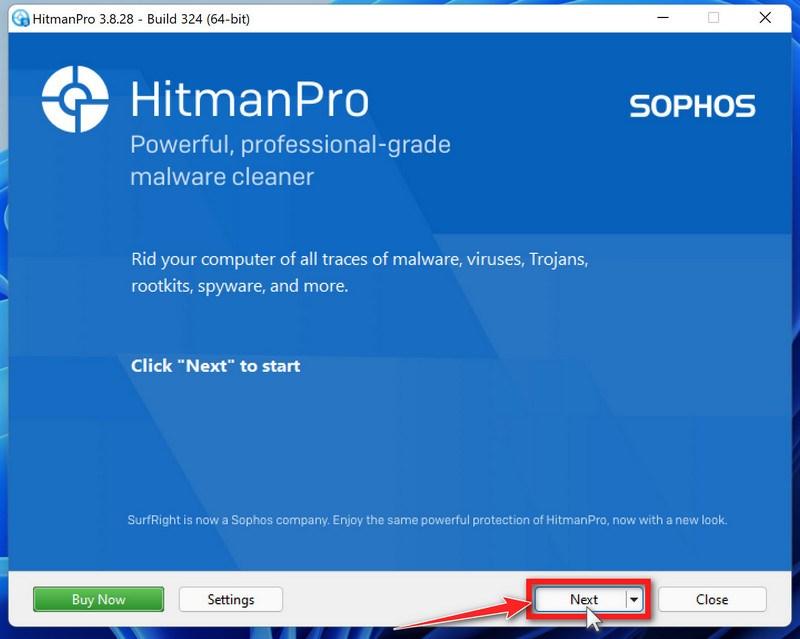
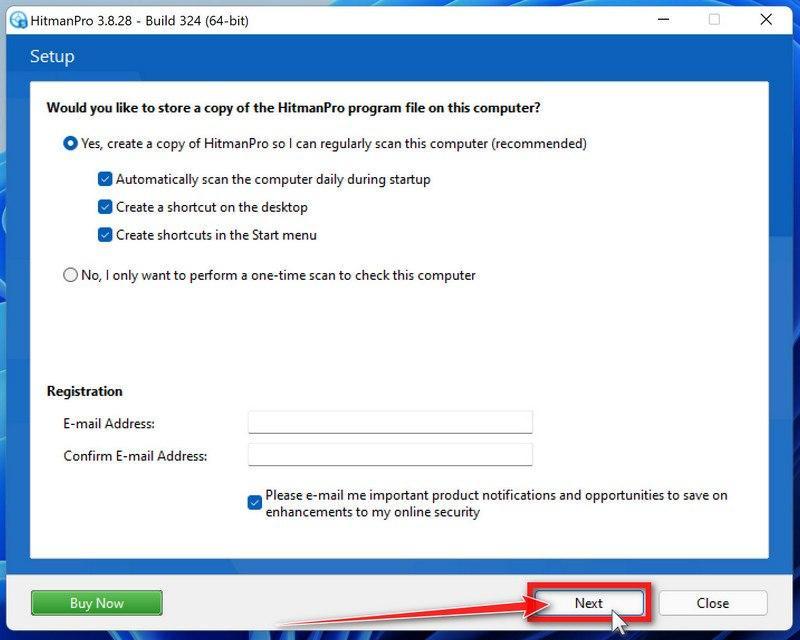
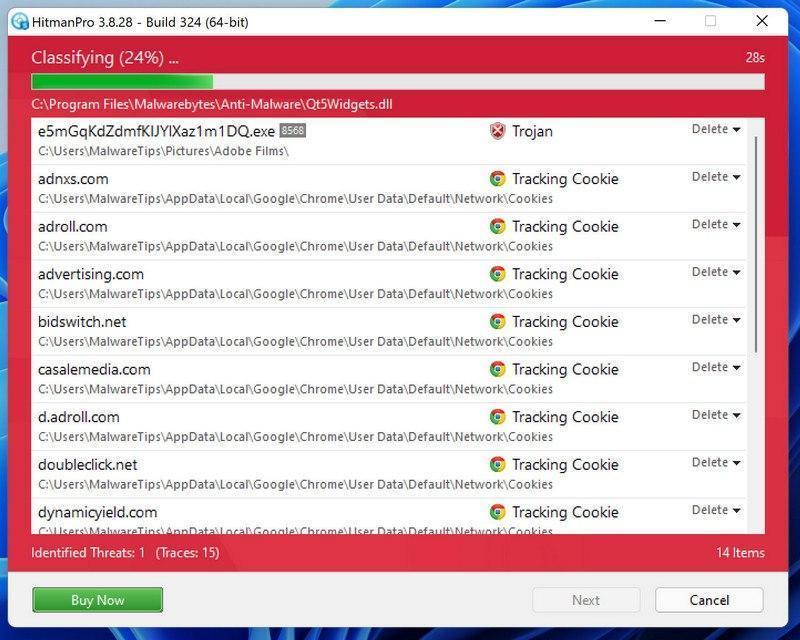
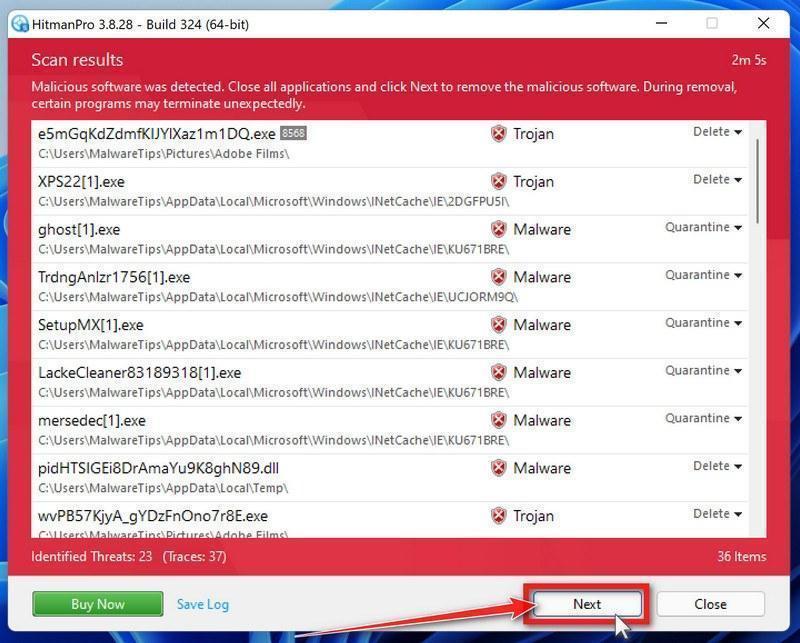
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 34 AdwCleaner Icon](https://malwaretips.com/blogs/wp-content/uploads/2018/09/AdwCleaner-Icon.png)
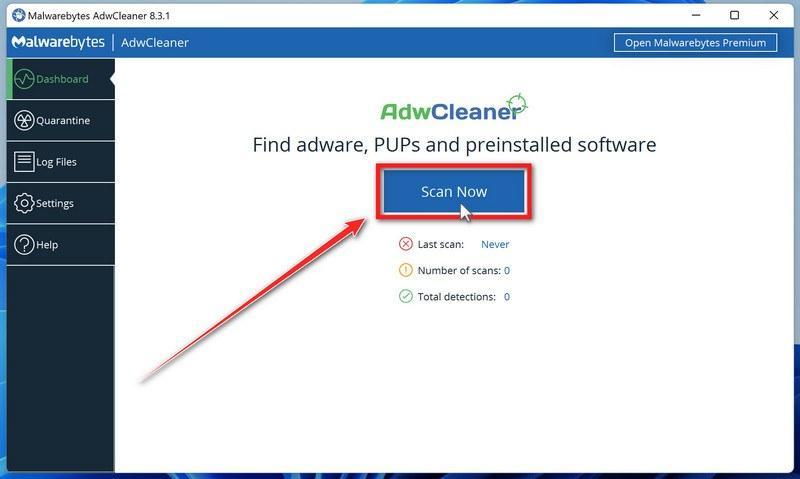
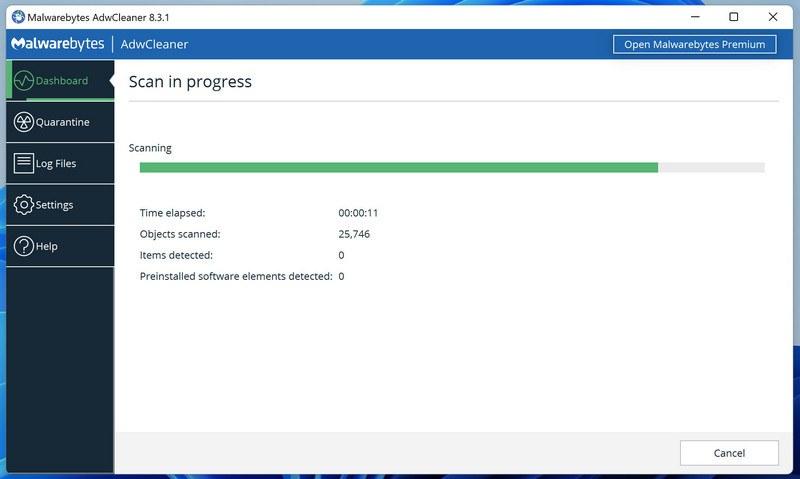
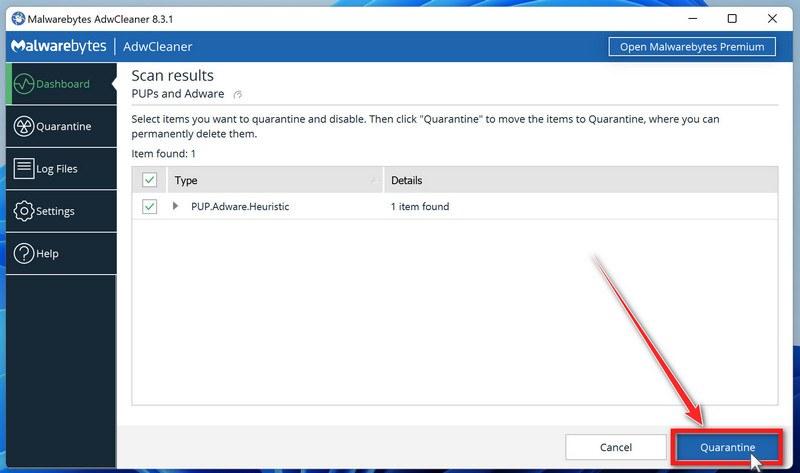
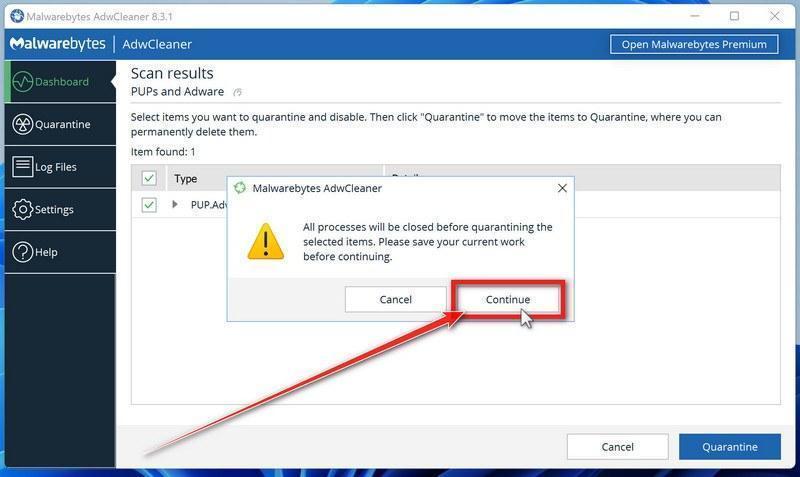
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 35 ESET logo](https://malwaretips.com/blogs/wp-content/uploads/2022/09/Eset-Logo.png)
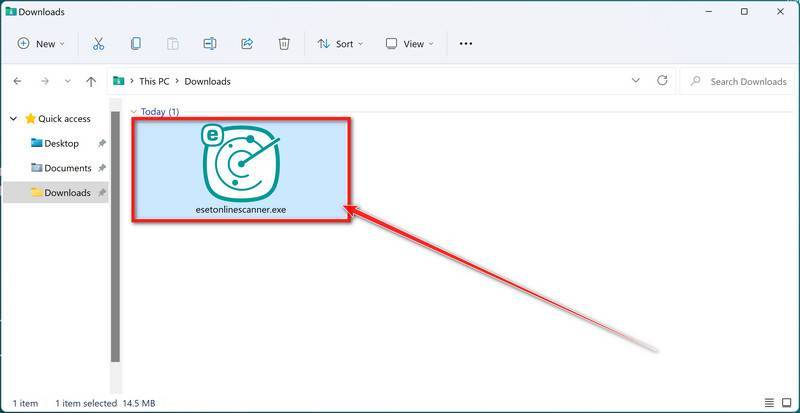
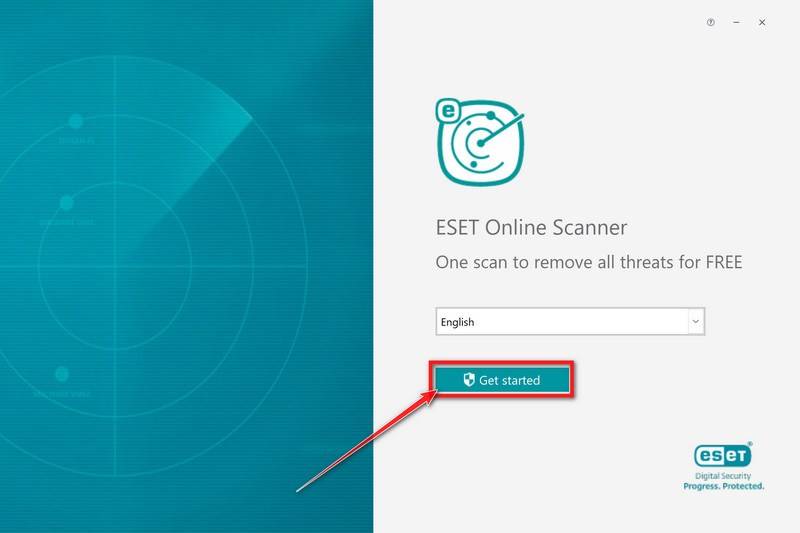
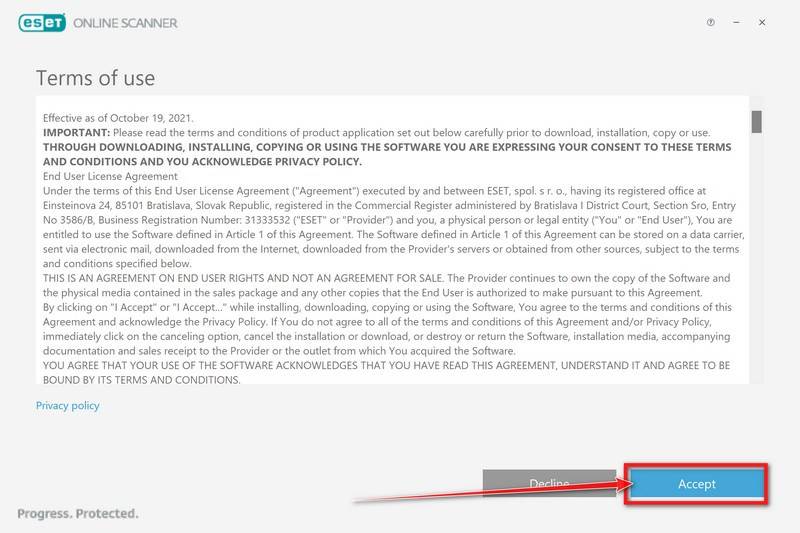
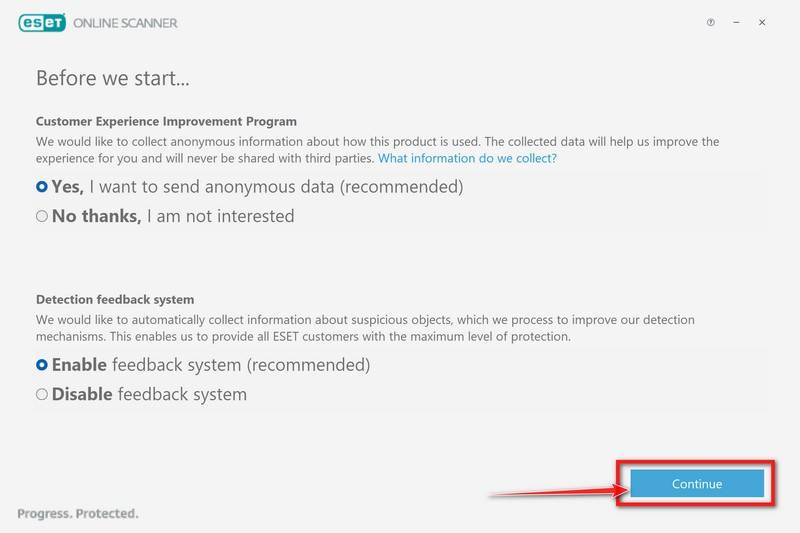
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 36 Search for Profiles in System Preferences](https://malwaretips.com/blogs/wp-content/uploads/2020/01/System-Preferences-MacOS.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 37 Remove malicious profiles from your Mac](https://malwaretips.com/blogs/wp-content/uploads/2020/01/Malicious-Profile.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 38 Open Finder](https://malwaretips.com/blogs/wp-content/uploads/2019/11/Open-Finder.jpg)
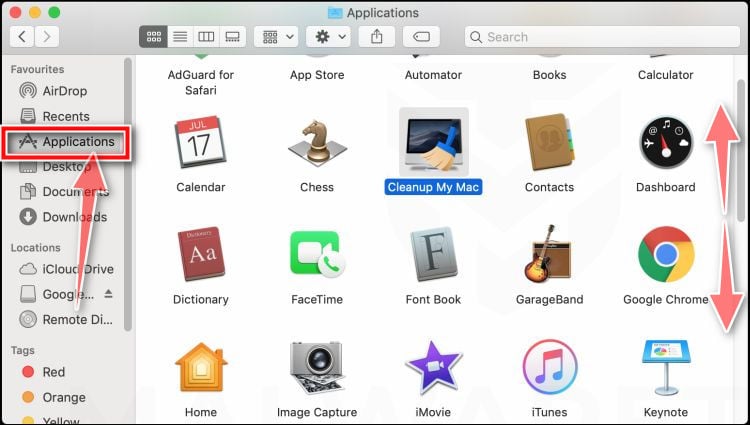
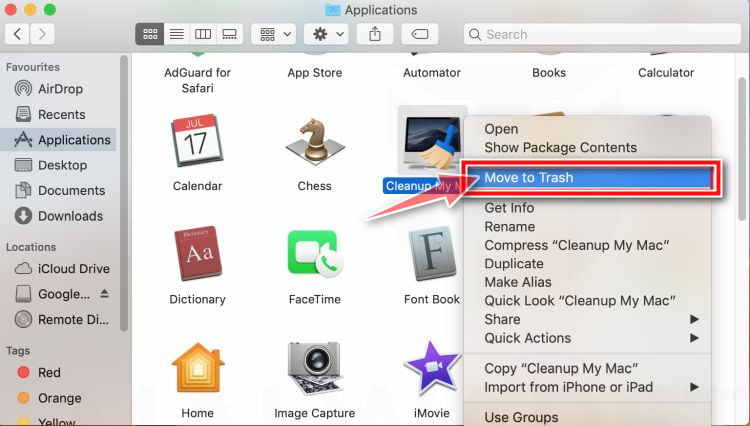
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 39 Empty Trash](https://malwaretips.com/blogs/wp-content/uploads/2019/11/Empty-Trash.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 40 Go to Folder mac](https://malwaretips.com/blogs/wp-content/uploads/2020/01/Go-to-folder-Mac.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 41 Type the commands in the Go to Folder window](https://malwaretips.com/blogs/wp-content/uploads/2020/01/Library-folders.jpg)
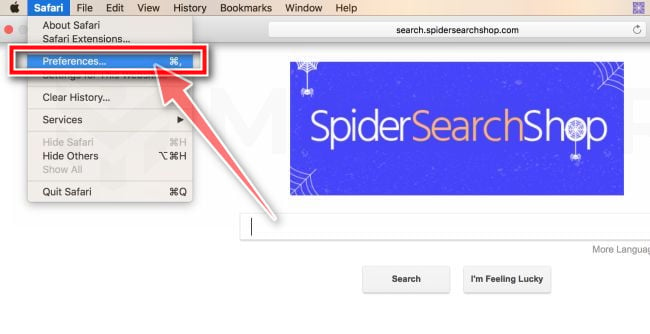
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 42 Change Homepage in Safari](https://malwaretips.com/blogs/wp-content/uploads/2018/08/Change-Homepage.jpg)
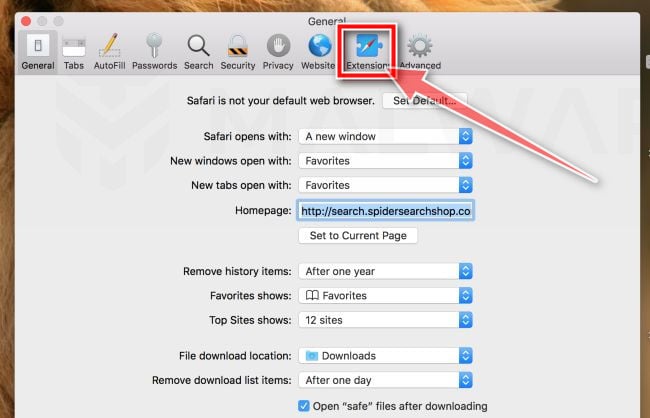
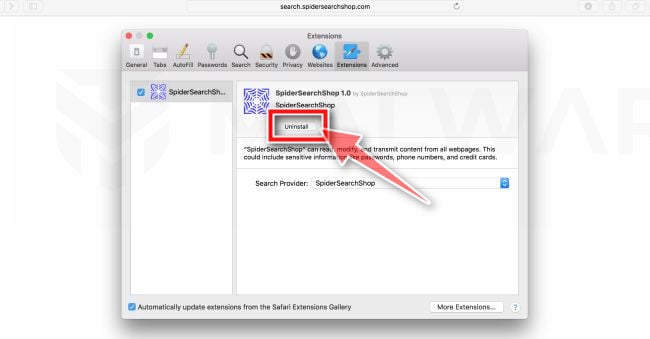
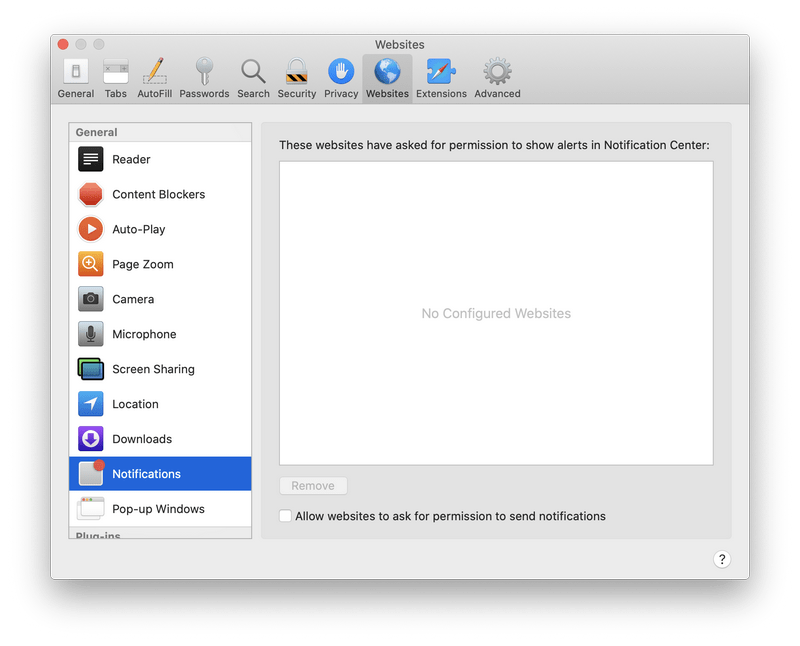
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 43 Click Manage Website Data](https://malwaretips.com/blogs/wp-content/uploads/2022/10/Manage-Website-Data.png)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 44 Click Remove All Website Data](https://malwaretips.com/blogs/wp-content/uploads/2022/10/Remove-All-Website-Data.png)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 45 Show Dev Bar](https://malwaretips.com/blogs/wp-content/uploads/2022/10/Show-Dev-Bar.png)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 46 empty cache](https://malwaretips.com/blogs/wp-content/uploads/2022/10/empty-cache.png)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 47 Click on the Chrome menu button then on the Settings button](https://malwaretips.com/blogs/wp-content/uploads/2022/10/Chrome-Reset-Mac-1.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 48 Click on Reset and Cleanup](https://malwaretips.com/blogs/wp-content/uploads/2022/10/Chrome-Reset-Mac-2.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 49 Reset Chrome](https://malwaretips.com/blogs/wp-content/uploads/2022/10/Chrome-Reset-Mac-3.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 50 Confirm Reset Chrome browser](https://malwaretips.com/blogs/wp-content/uploads/2022/10/Chrome-Reset-Mac-4.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 51 Chrome Sync Reset](https://malwaretips.com/blogs/wp-content/uploads/2022/10/Chrome-Sync-Reset.jpg)

![How to Remove a Trojan Virus from Windows [Rmoval Guide] 52 Image - Troubleshooting Information option in Firefox Mac](https://malwaretips.com/blogs/wp-content/uploads/2022/10/Reset-Firefox-Mac-2.jpg)
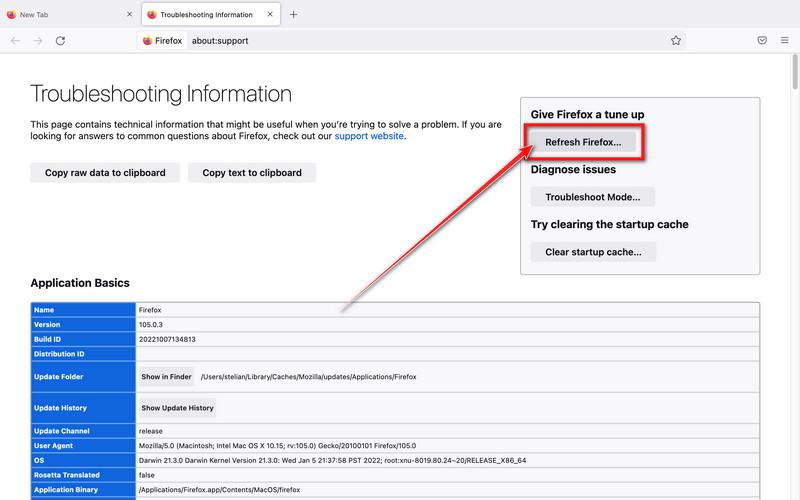
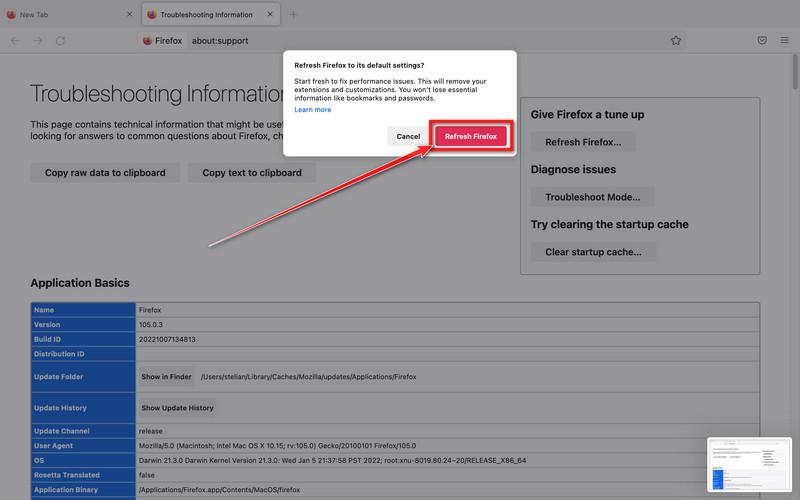
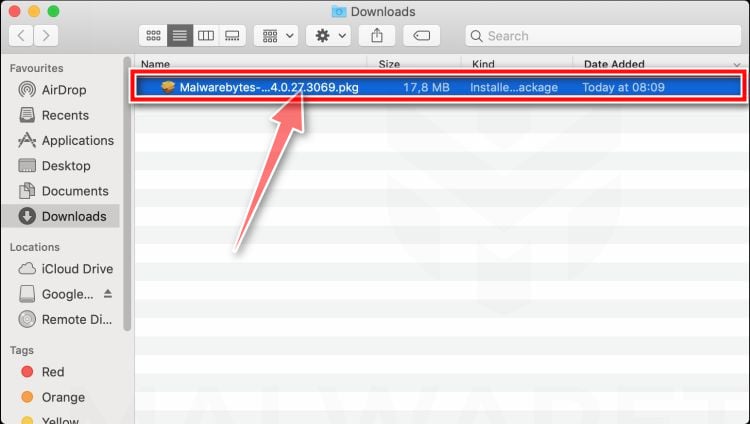
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 53 Click Continue to install Malwarebytes for Mac](https://malwaretips.com/blogs/wp-content/uploads/2019/11/Malwarebytes-Mac-Installer-Step-1.jpg)
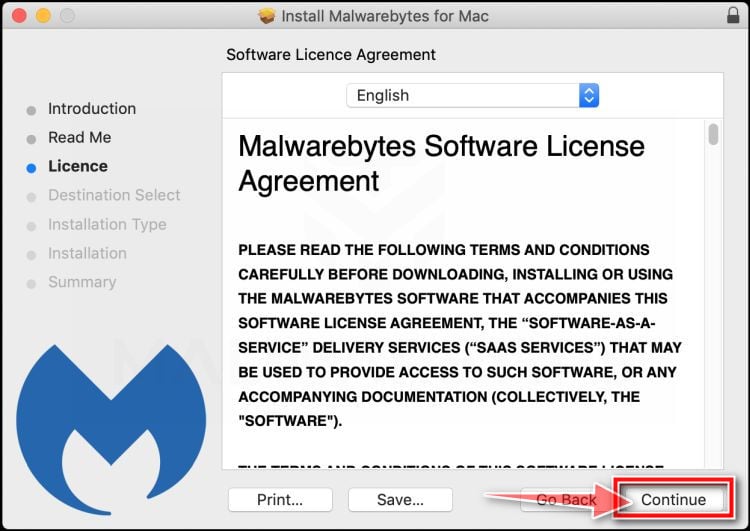
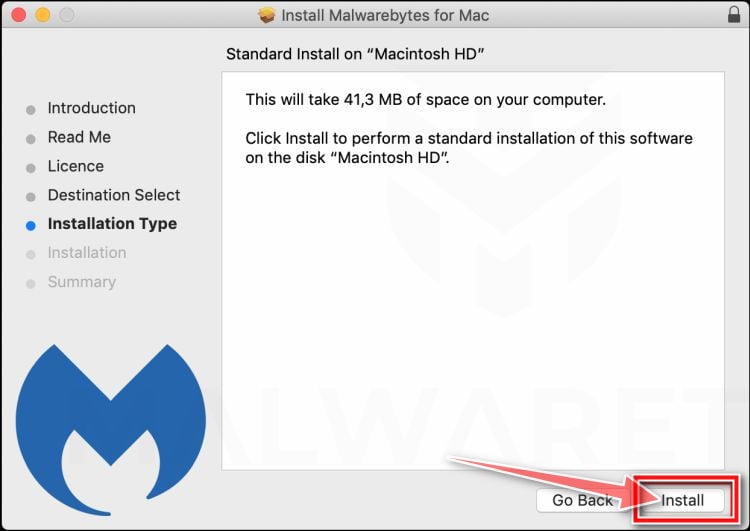
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 54 Select Personal Computer or Work Computer mac](https://malwaretips.com/blogs/wp-content/uploads/2019/11/Malwarebytes-Mac-Select-Personal-Computer.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 55 Click on Scan button to start a system scan Mac](https://malwaretips.com/blogs/wp-content/uploads/2019/11/Malwarebytes-Mac-Click-Scan.jpg)
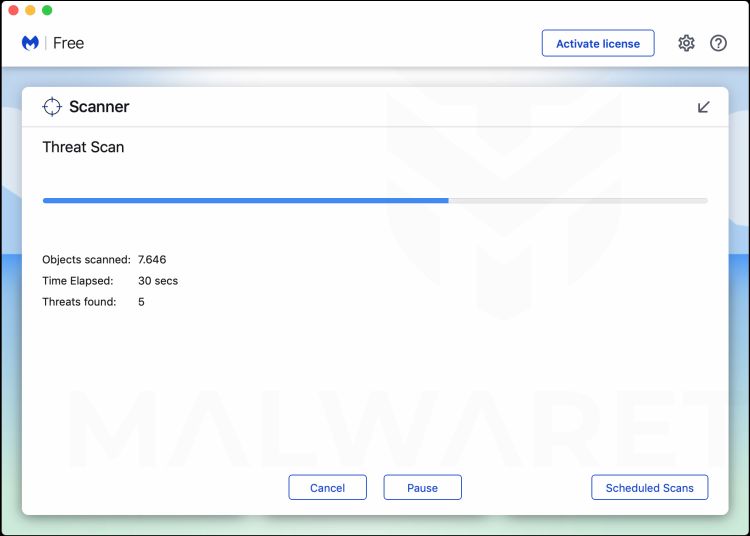
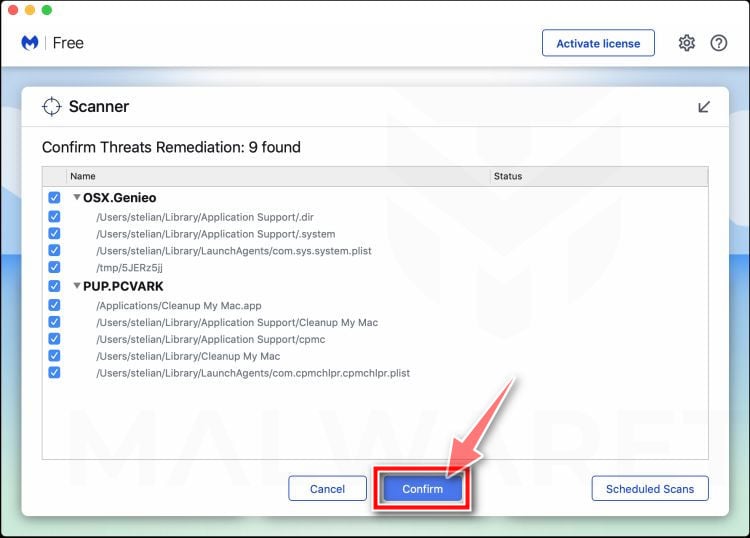
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 56 Malwarebytes For Mac requesting to restart computer](https://malwaretips.com/blogs/wp-content/uploads/2019/11/Malwarebytes-Mac-Restart.jpg)
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 57 Settings app in Android](https://malwaretips.com/blogs/wp-content/uploads/2020/05/Menu-Settings.jpg)
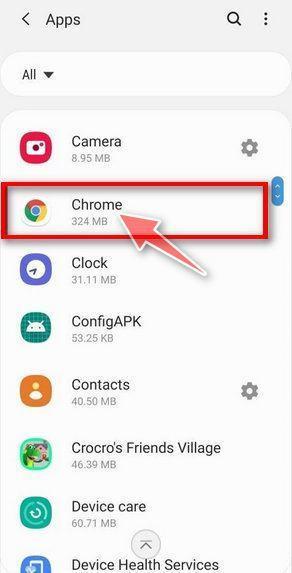
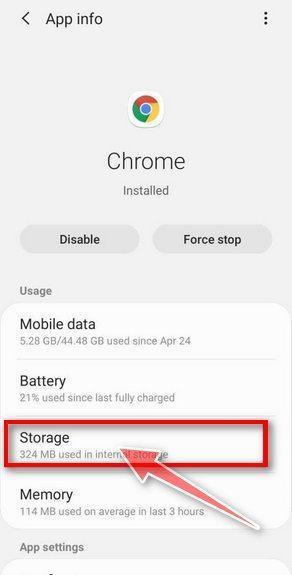
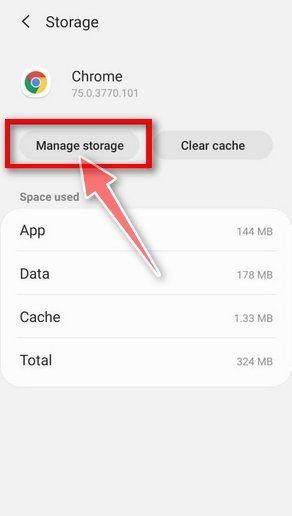
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 58 Tap on Apps](https://malwaretips.com/blogs/wp-content/uploads/2020/05/Android-Open-Settings.jpg)
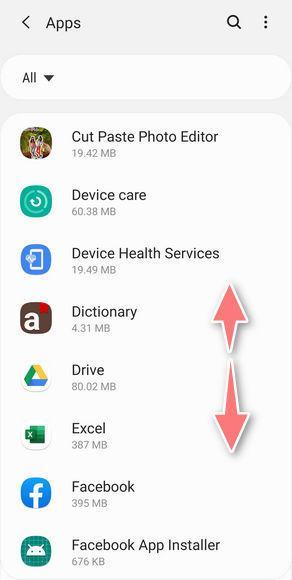
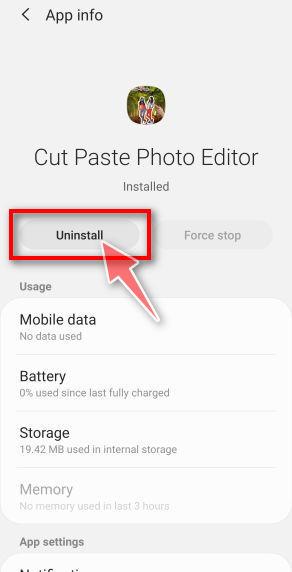
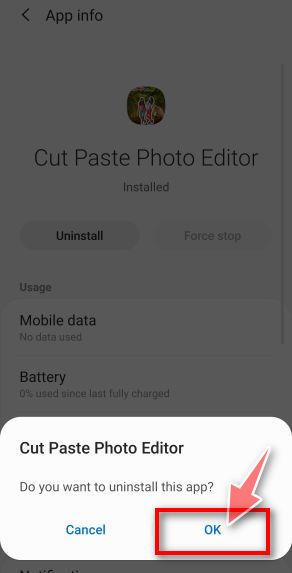
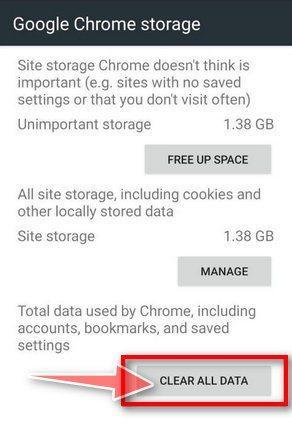
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 61 Tap Ok to restore default settings](https://malwaretips.com/blogs/wp-content/uploads/2020/05/Chrome-Android-Confirm-Clean-Data-1.jpg)
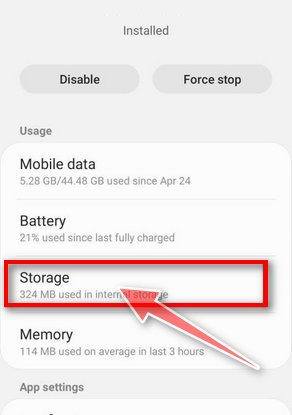
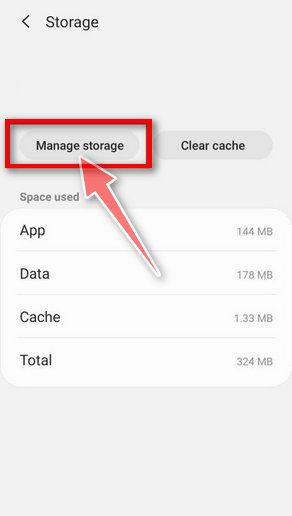

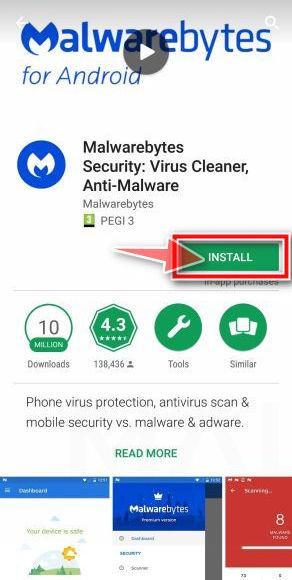
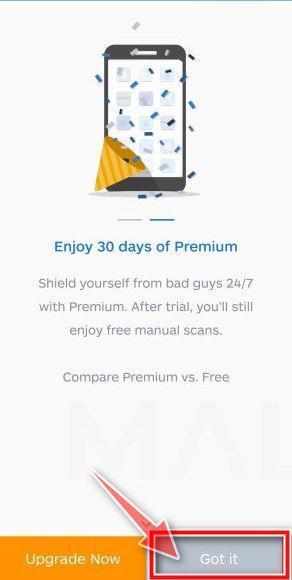
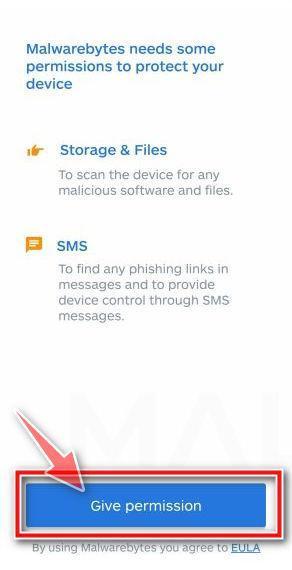
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 70 Malwarebytes for Android - Open App](https://malwaretips.com/blogs/wp-content/uploads/2020/05/Malwarebytes-for-Android-Open-App.jpg)
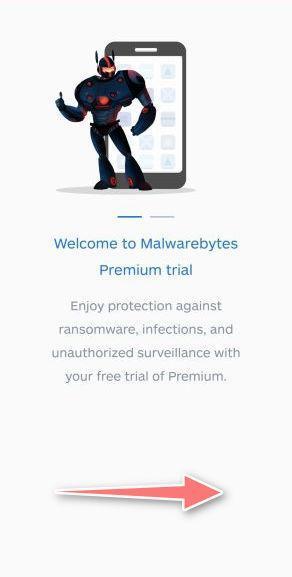
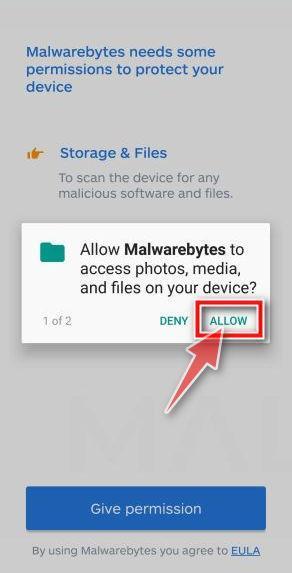
![How to Remove a Trojan Virus from Windows [Rmoval Guide] 71 Malwarebytes fix issue](https://malwaretips.com/blogs/wp-content/uploads/2020/05/Malwarebytes-for-Android-Fix-Issues.jpg)