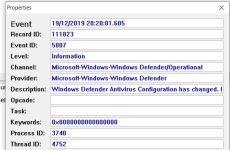
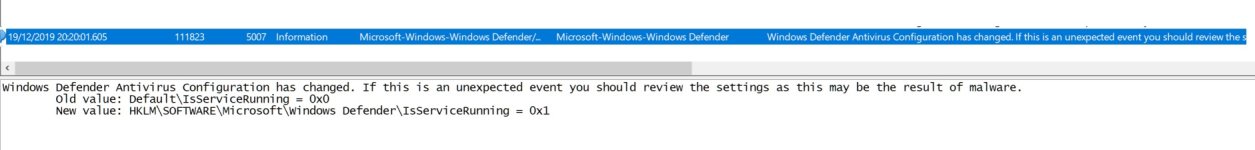
- Mar 29, 2018
- 8,061
I already created a similar application (Casual User Protection) :
... I plan to finish Hard_Configurator first, and then I will probably finish CUP.
So this is (in part) why we have seen so little of you on the forum lately. Up to your old tricks again! Looking good ... !