The new and dangerous Astaroth malware:
In the case of Astaroth, attackers hide binary data inside the ADS of the file
desktop.ini, without changing the file size. By doing this, the attackers create a haven for the payloads, which are read and decrypted on the fly.
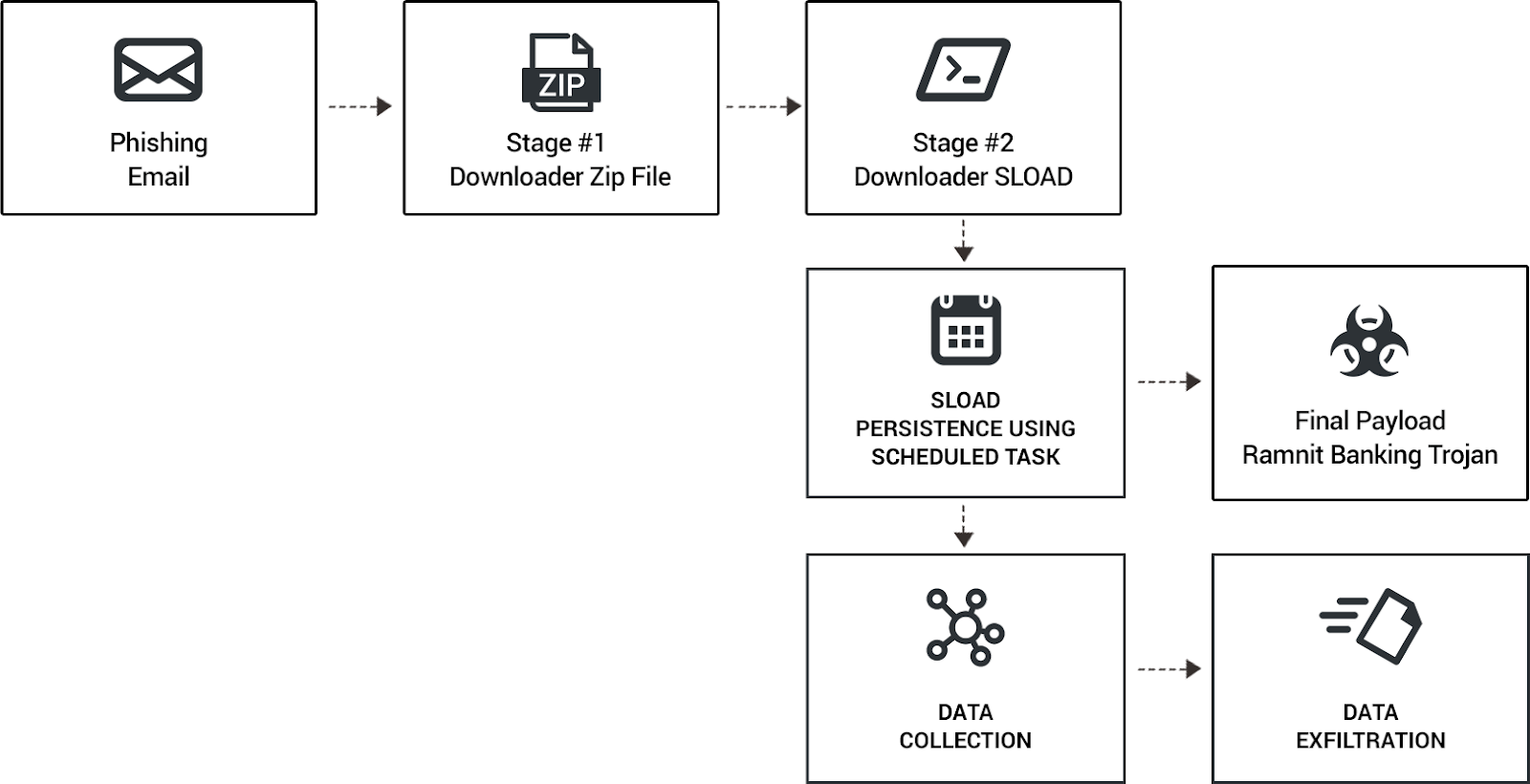
Astaroth is back sporting significant changes. The updated attack chain maintains Astaroth’s complex, multi-component nature and continues its pattern of detection evasion.

www.microsoft.com
So, how can this be stopped with H_C settings?
After the user downloads the malware and runs the unpacked content, the shortcut (LNK file) is normally executed which will be blocked by SRP. Even if the user applied the settings that allowed shortucts, then the shortcut normally runs JavaScript file via command-line (BAT commands are included in the shortcut - not in the BAT file), and the script will be blocked by SRP (blocked Windows Script Host).
This malware would be blocked by any predefined H_C setting profile (except All_OFF). It could be also stopped by blocking some Sponsors in H_C (bitsadmin.exe or ExtExport.exe), but this is not necessary (as usual) because of the previous protective layers.
The malware is prepared to avoid AV protection and can bypass SysHardener (if "Turn Off Windows Script Host" is unticked). SysHardener has an option to block the outbound connections of bitsadmin.exe, but unfortunately, this will not stop Astaroth from downloading payloads.
Edit.
SysHardener has several options to restrict Windows Script Host. Some options will block only such scripts when manually executed by the user (unassociated script extensions) and the second option which blocks all attempts of running such scripts (by the user or any process - including malware).