Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
Certutil is already added. Bitsadmin and CMD do not make outbound connections, but trigger other processes that do this for them. For example, bitsadmin.exe triggers svchost.exe. The CMD will trigger Bitsadmin, Wscript, Cscript, PowerShell, Certutil, or other LOLBins.Maybe cmd.exe, bitsadmin, certutil.exe?
Here's one related to using certutil.exe to download malwares
Here's another detailed analysis about LOLbins manipulation by Ramnit trojan that you might be interested to read
CertUtil.exe Could Allow Attackers To Download Malware While Bypassing AV
Windows has a built-in program called CertUtil, which can be used to manage certificates in Windows. Using this program you can install, backup, delete, manage, and perform various functions related to certificates and certificate stores in Windows.www.bleepingcomputer.com
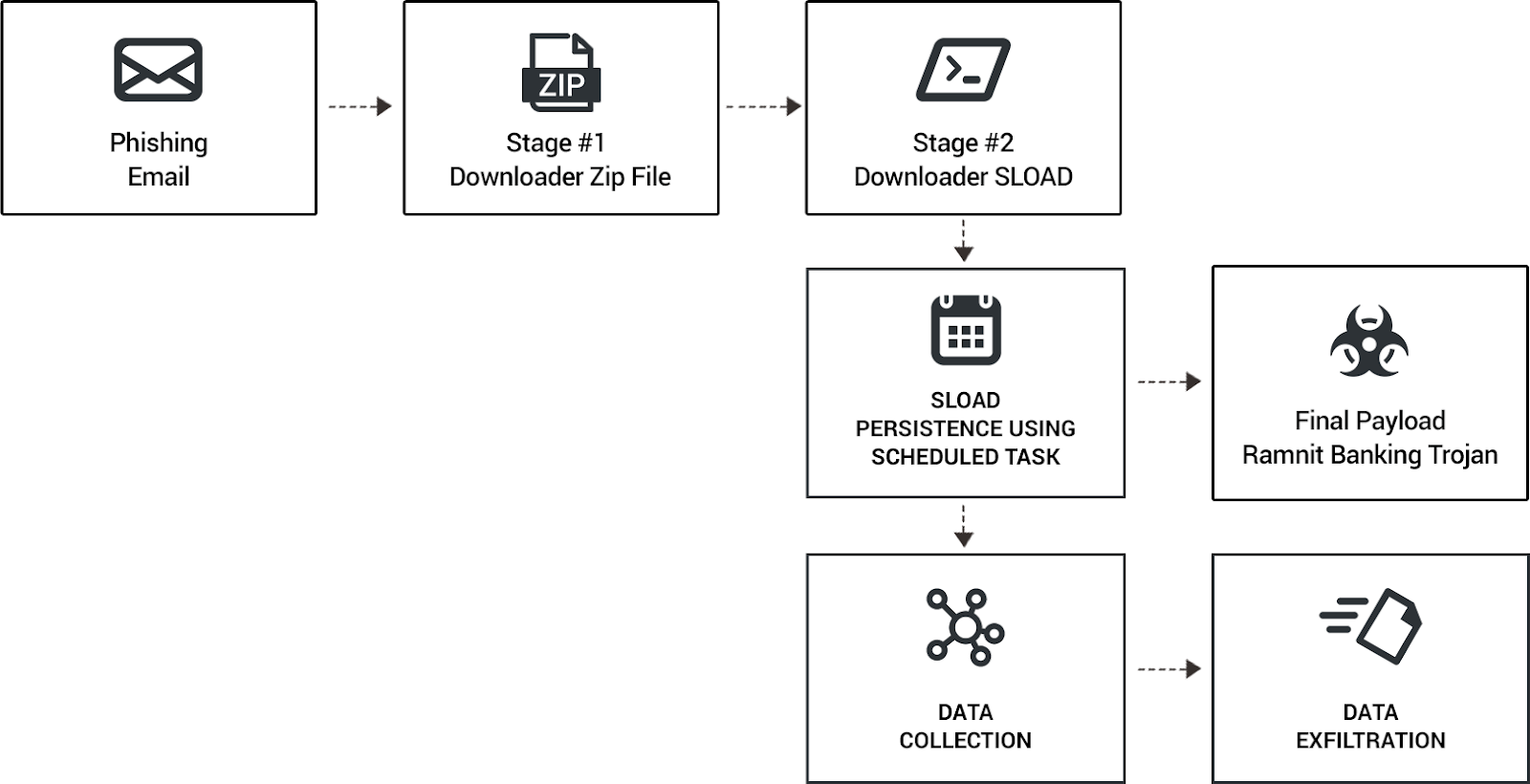
LOLbins and trojans: How the Ramnit Trojan spreads via sLoad in a cyberattack
Cybereason detected an evasive infection technique used to spread a variant of the Ramnit banking Trojan as part of an Italian spam campaign. We investigate this attack, its use of sLoad, and its adoption of LOLbins to minimize discovery.www.cybereason.com


