Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,908
Post updated in January 2025.
The current version can be downloaded from GitHub:
https://github.com/AndyFul/Hard_Configurator/raw/master/Hard_Configurator_setup_7.0.0.1.exe
The previous version can be downloaded from Softpedia:
https://www.softpedia.com/get/Tweak/System-Tweak/Hard-Configurator.shtml
WARNING!
The fake domain hard-configurator.com is used by some malicious actors. Please do not use it. Someone tries to fool people who want to get information about Hard_Configurator.
Support for Windows 11 22H2 and later versions was added in the version 6.1.1.1.
Windows 11 ver. 22H2 (fresh installation) turns off by default Software Restriction Policies. So, Hard_Configurator ver. 6.0.1.1 (and prior) could not use SRP (restrictions from the left panel in H_C ). This issue was corrected in version 6.1.1.1. The current version can also work with enabled Smart App Control.
Developer website:

 github.com
github.com
Hard_Configurator was created after a discussion on the below treads:
https://www.wilderssecurity.com/thr...ith-lua-and-srp-even-without-ultimate.232857/
Secure Windows - Software restriction Policies to Windows Home
Windows Pro owner? Use Software Restriction Policies!
Poll - Do you use security reg tweaks?
Run by SmartScreen utility
Microsoft documentation for Software Restriction Policies:
 This documentation was made for Windows Server (2012, 2016, 2019, and 2022), but SRP works the same on Windows 7, 8, 8.1, 10, and 11.
This documentation was made for Windows Server (2012, 2016, 2019, and 2022), but SRP works the same on Windows 7, 8, 8.1, 10, and 11.
Software Restriction Policies cannot work on the same computer together with Applocker Policies and also with Child Account (created via Microsoft Family Safety).
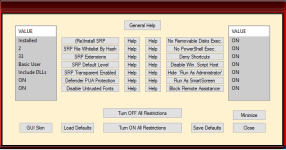
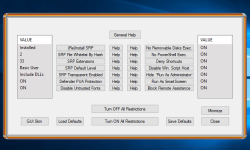
What is Hard_Configurator for?
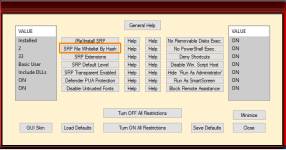
This program can configure Windows built-in security to harden the system. When you close Hard_Configurator it closes all its processes. The real-time protection comes from the reconfigured Windows settings. Hard_Configurator can be seen as a Medium Integrity Level smart default-deny setup, which is based on SRP + Application Reputation Service (forced SmartScreen) + Windows hardening settings (restricting vulnerable features).
Hard_Configurator makes changes in the Windows Registry to accomplish the tasks enumerated below:
Many of the above tasks can be done by using Windows RegEdit. Anyway, with Hard_Configurator, it can be done more quickly and safely.
How to be unhappy with Hard_Configurator:

The current version can be downloaded from GitHub:
https://github.com/AndyFul/Hard_Configurator/raw/master/Hard_Configurator_setup_7.0.0.1.exe
The previous version can be downloaded from Softpedia:
https://www.softpedia.com/get/Tweak/System-Tweak/Hard-Configurator.shtml
WARNING!
The fake domain hard-configurator.com is used by some malicious actors. Please do not use it. Someone tries to fool people who want to get information about Hard_Configurator.
Support for Windows 11 22H2 and later versions was added in the version 6.1.1.1.
Windows 11 ver. 22H2 (fresh installation) turns off by default Software Restriction Policies. So, Hard_Configurator ver. 6.0.1.1 (and prior) could not use SRP (restrictions from the left panel in H_C ). This issue was corrected in version 6.1.1.1. The current version can also work with enabled Smart App Control.
Developer website:
GitHub - AndyFul/Hard_Configurator: GUI to Manage Software Restriction Policies and harden Windows Home OS
GUI to Manage Software Restriction Policies and harden Windows Home OS - AndyFul/Hard_Configurator
Hard_Configurator was created after a discussion on the below treads:
https://www.wilderssecurity.com/thr...ith-lua-and-srp-even-without-ultimate.232857/
Secure Windows - Software restriction Policies to Windows Home
Windows Pro owner? Use Software Restriction Policies!
Poll - Do you use security reg tweaks?
Run by SmartScreen utility
Microsoft documentation for Software Restriction Policies:

Software Restriction Policies Technical Overview
Learn about software restriction policies, when and how to use the feature, and what changes have been implemented in past releases.
learn.microsoft.com
Software Restriction Policies cannot work on the same computer together with Applocker Policies and also with Child Account (created via Microsoft Family Safety).
What is Hard_Configurator for?
This program can configure Windows built-in security to harden the system. When you close Hard_Configurator it closes all its processes. The real-time protection comes from the reconfigured Windows settings. Hard_Configurator can be seen as a Medium Integrity Level smart default-deny setup, which is based on SRP + Application Reputation Service (forced SmartScreen) + Windows hardening settings (restricting vulnerable features).
Hard_Configurator makes changes in the Windows Registry to accomplish the tasks enumerated below:
- Enabling Software Restriction Policies (SRP) in Windows Home editions.
- Changing SRP Security Levels, Enforcement options, and Designated File Types.
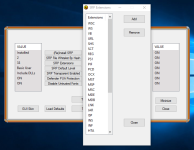
- Whitelisting files in SRP by path (also with wildcards) and by hash.
- Blocking the vulnerable system executables via SRP.
- Protecting (deny execution) writable subfolders in %WinDir% folder (via SRP).
- Restricting shortcut execution to some folders only (via SRP).
- Enabling Windows Defender advanced settings, like PUA protection, ASR rules, Network Protection, etc.
- Blocking outbound connections of many LOLBins and user applications.
- Filtering Windows Event Log for blocked outbound connections.
- Protecting against weaponized documents, when MS Office and Adobe Acrobat Reader XI/DC are used to open them.
- Disabling PowerShell script execution (Windows 7+).
- Securing PowerShell by Constrained Language mode (SRP, PowerShell 5.0+)
- Disabling execution of scripts managed by Windows Script Host.
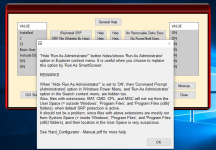
- Removing the "Run as administrator" option from the Explorer right-click context menu.
- Forcing the SmartScreen for files without 'Mark Of The Web' (Windows 8+).
- Disabling Remote Desktop, Remote Assistance, Remote Shell, and Remote Registry.
- Disabling execution of 16-bit applications.
- Securing Shell Extensions.
- Disabling SMB protocols.
- Disabling program elevation on Standard User Account.
- Disabling Cached Logons.
- Filtering Windows Event Log for blocked file execution events (Nirsoft FullEventLogView).
- Filtering autoruns from the User Space, and script autoruns from anywhere (Sysinternals Autorunsc).
- Turning ON/OFF all the above restrictions.
- Restoring Windows Defaults.
- Making System Restore Point.
- Using predefined setting profiles for Windows 7, Windows 8, and Windows 10.
- Saving the chosen restrictions as a profile, and restoring when needed.
- Backup management for Profile Base (whitelist profiles and setting profiles).
- Changing GUI skin.
- Updating application.
- Uninstalling application (Windows defaults restored).
Many of the above tasks can be done by using Windows RegEdit. Anyway, with Hard_Configurator, it can be done more quickly and safely.
How to be unhappy with Hard_Configurator:
- Install Hard_Configurator.
- Ignore the info displayed during the installation.
- Do not read the help files.
- Do not read the Manual.
Last edited: