Will protecting WSH against this attack help?
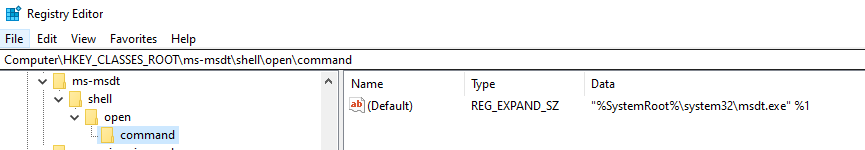
Windows MSDT zero-day now exploited by Chinese APT hackers
Windows MSDT zero-day now exploited by Chinese APT hackers
Yes.Will protecting WSH against this attack help?
Windows MSDT zero-day now exploited by Chinese APT hackers

 malwaretips.com
malwaretips.com

 malwaretips.com
malwaretips.com
Now, that's how a test should be done, unlike.....Here is a short video about my test:

This event could happen when:Hi Andy, every 2 weeks or so I get one of these blocks, I assume its nothing but could you enlighten me please. I apologize if I asked this before, I don't remember.
Event[0]:
Event Id = 866
Local Time: 2022/06/15 13:37:03
EventRecordID = 33903
ActivityID = '{0314c0cb-d11f-44bc-96dd-acd0fce91e71}'
Execution ProcessID = '796' ThreadID='3728'
Computer = DESKTOP-L1SV63C
UserID='S-1-5-21-1777632603-4013640730-1325600334-1001'
Attempted Path = C:\Program Files\WindowsApps\Microsoft.DesktopAppInstaller_1.17.10941.0_x64__8wekyb3d8bbwe\WindowsPackageManagerServer.exe
SRP Rule GUID = {1016bbe0-a716-428b-822e-5e544b6a3300}
Description: File blocked via SRP Rule GUID for Disallowed rule C:\Program Files\WindowsApps\Microsoft.DesktopAppInstaller*
I do not think so. You cannot update the desktop application by using Microsoft Store (so far).Thank you. I guess this happens when I go to the Microsoft store and update my apps.
There has to be a rule configured manually via H_C (not default H_C; not sure how it got in there) that contains the * wildcard for the WindowsApps\MicrosoftDesktopAppInstaller folder that looks like :Ok, I see where you coming from now...however... I have 2 blocks from this morning, coincidently I opened the MS store twice this morning to check for updates (there were none.) Also, I very rarely try to install programs from the MS store. I am going to open store again and see if I get a block, will let you know.
Edit: Yup, another block after opening the MS store.
Interesting. Is the block present if you open Microsoft Store and do nothing?Edit: Yup, another block after opening the MS store.
Yes.Interesting. Is the block present if you open Microsoft Store and do nothing?
A ha, another one, proves I'm not going insane.I just have to click on the Microsoft Store icon to get this message...in SWH.
View attachment 267522