The CUP project is evolving. Here are some screenshots.
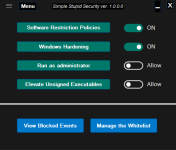
CUP with H_C (beta) Recommended Settings:
The 4 Hardening Rules can be explicitly seen (3 Disabled and 'Adobe + VBA').
When one chooses the hardening option, for example, * Admin Windows Script Host * then the alert is displayed:
After choosing <Disable>, the * Admin Windows Script Host * setting changes to Disabled.
The number of Hardening Rules changes from 4 to 5.
The "SRP Level" depends on EXE and MSI restrictions. It cannot be changed in CUP, but can be loaded via setting profile:
- Level 1 - EXE and MSI files not blocked (like in the H_C profile: Basic Recommended Settings).
- Level 2 - EXE files not blocked. MSI files blocked, except when in ProgramData or user AppData hidden folders (like in the H_C profile: Avast Hardened Mode Aggressive).
- Level 3 - EXE and MSI files blocked in UserSpace, except when in ProgramData or user AppData hidden folders (like in the H_C Recommended Settings).
- Level 4 - EXE and MSI files blocked in UserSpace (like in the H_C Strict Recommended Settings).